Using Okta MFA for Opal logins
For logins, you must do 3 things:- Setup Okta as your SAML provider. For instructions, see here.
- In Okta, configure your Opal SAML app to require MFA for login.
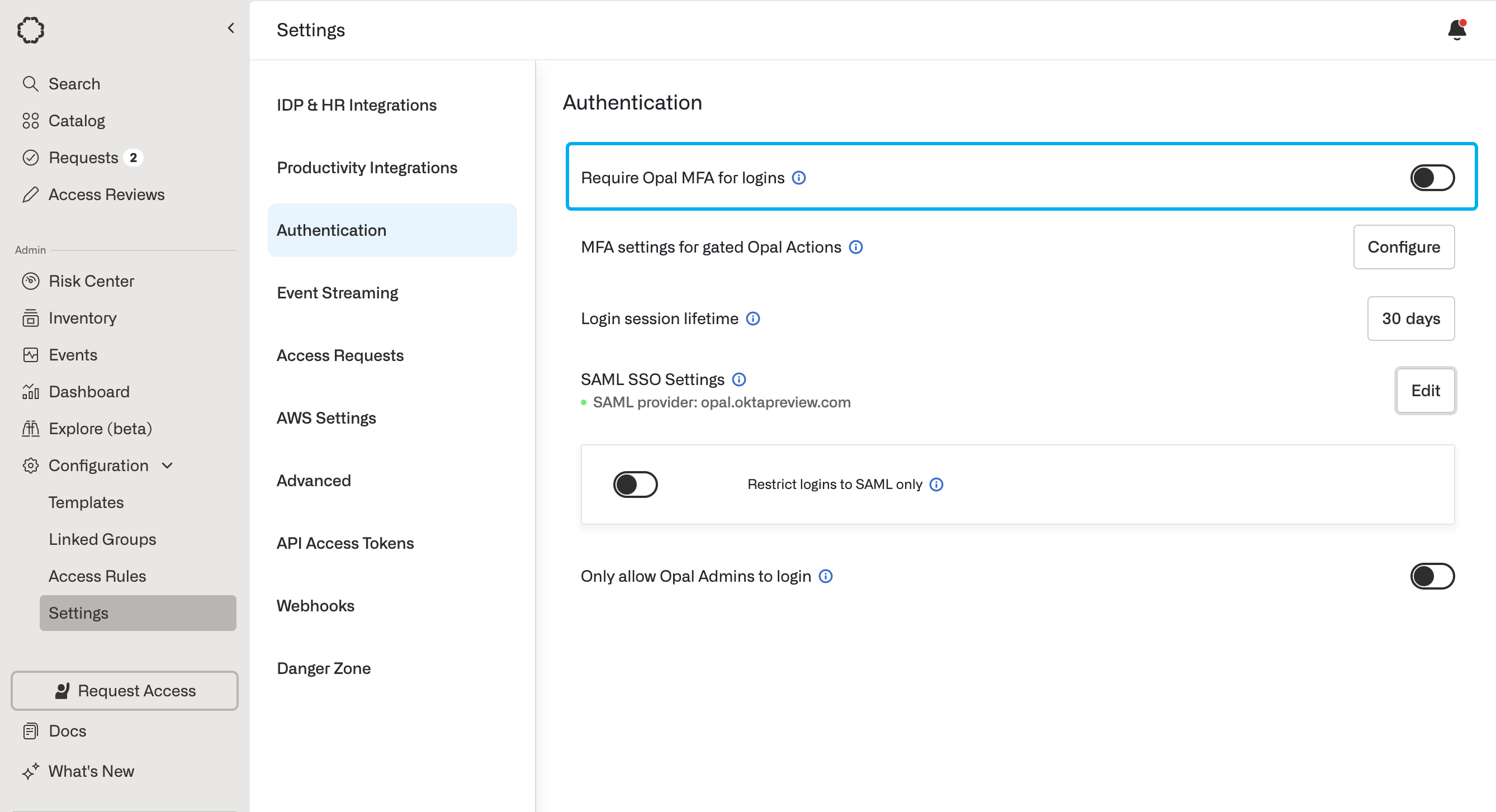
- In Opal, ensure that the Require Opal MFA for logins setting is off.
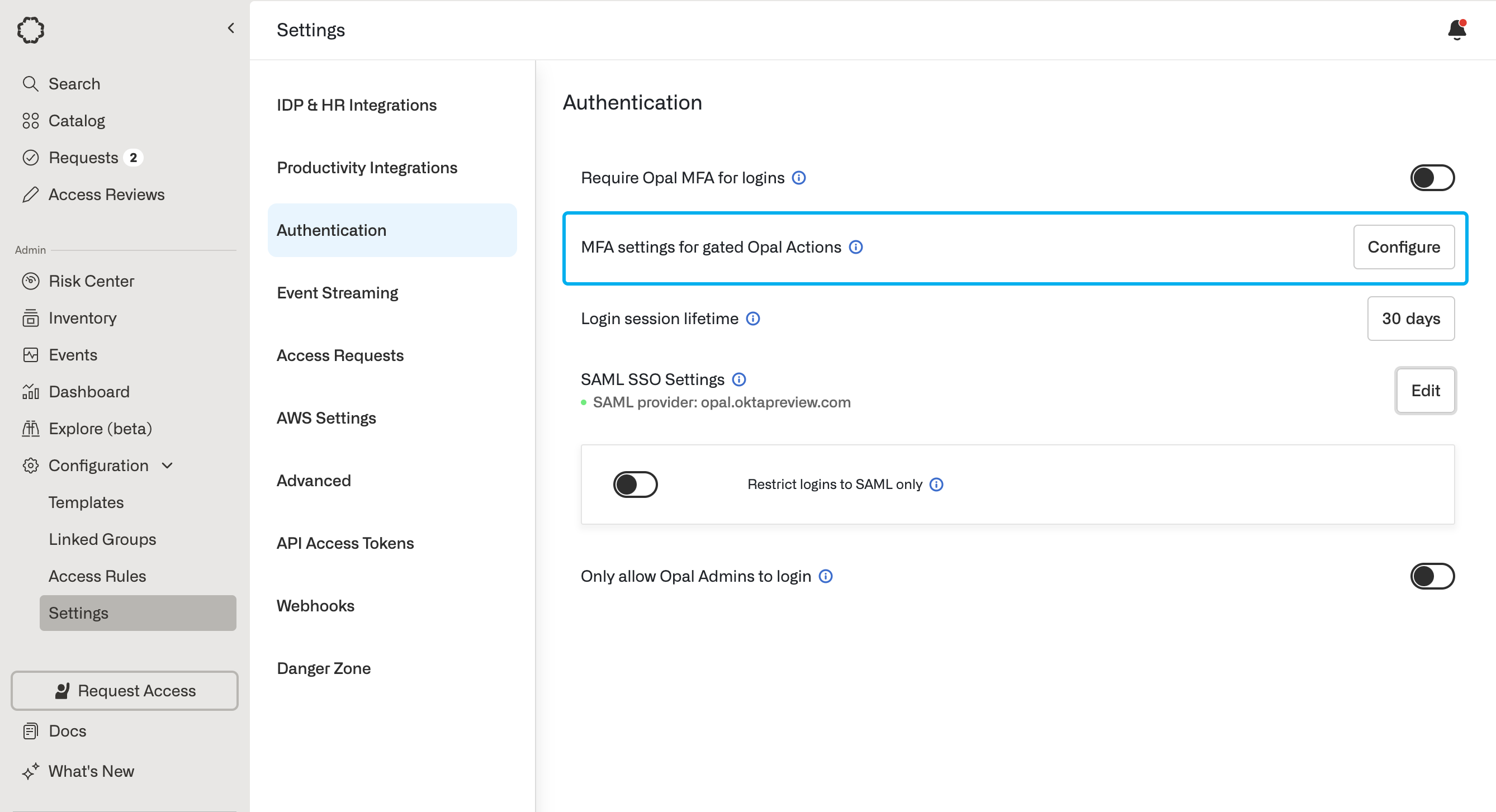
Using Okta MFA for Opal actions: requesting, approving, connecting [Legacy]
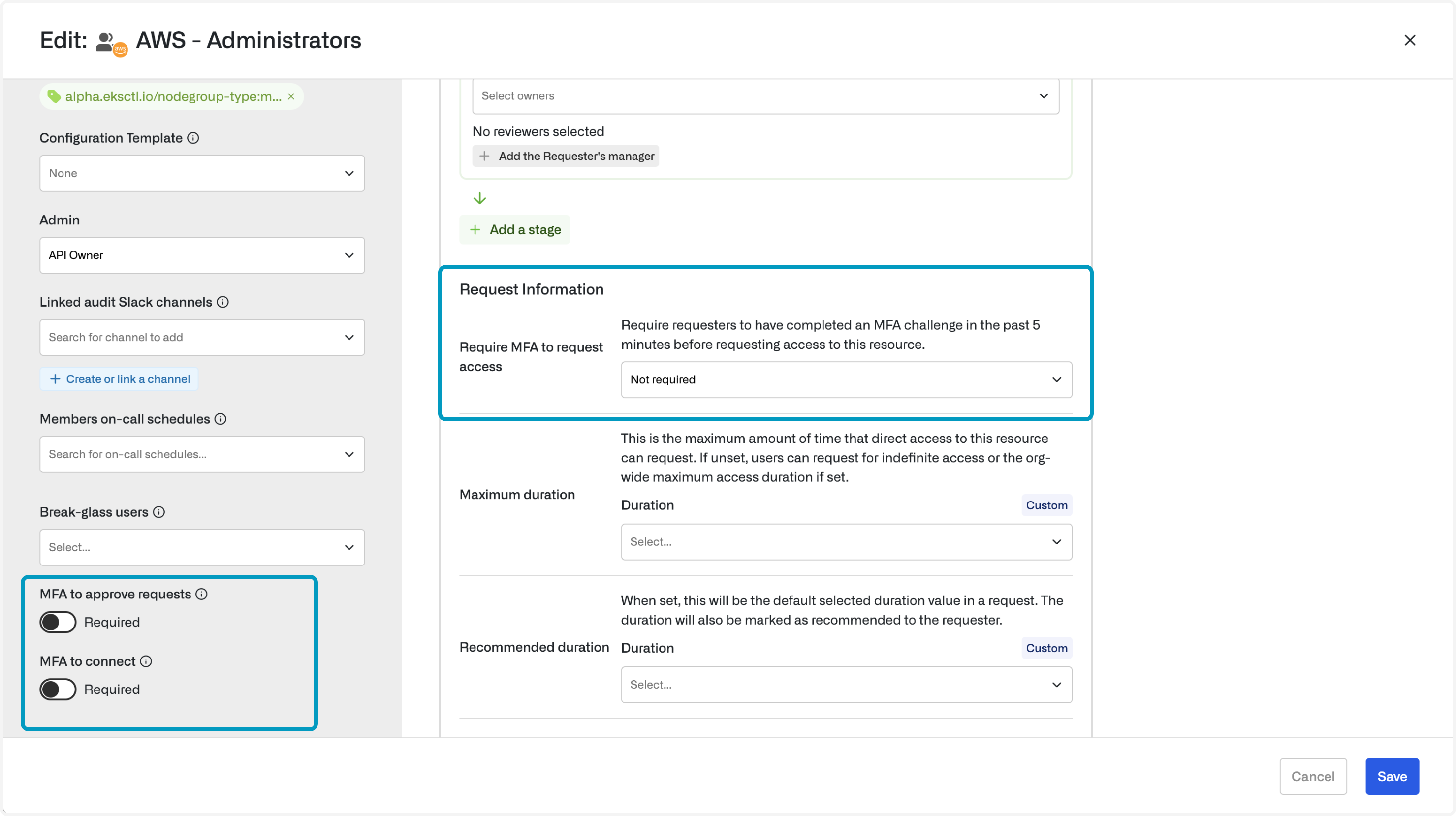
First, go to the resource(s) you want to require MFA for and click “Edit.” Then, in the left pane, toggle on the desired setting:- MFA to approve requests requires reviewers to have completed an MFA in the past 5 minutes prior to approving a request.
- MFA to connect (applies to select resource types) requires the user to have completed an MFA in the past 5 minutes prior to connecting to a resource.
Requirements for Okta Verify Push
When a push notification is sent to the Okta Verify app, the location associated with the user agent is included to prevent phishing. Here is an example: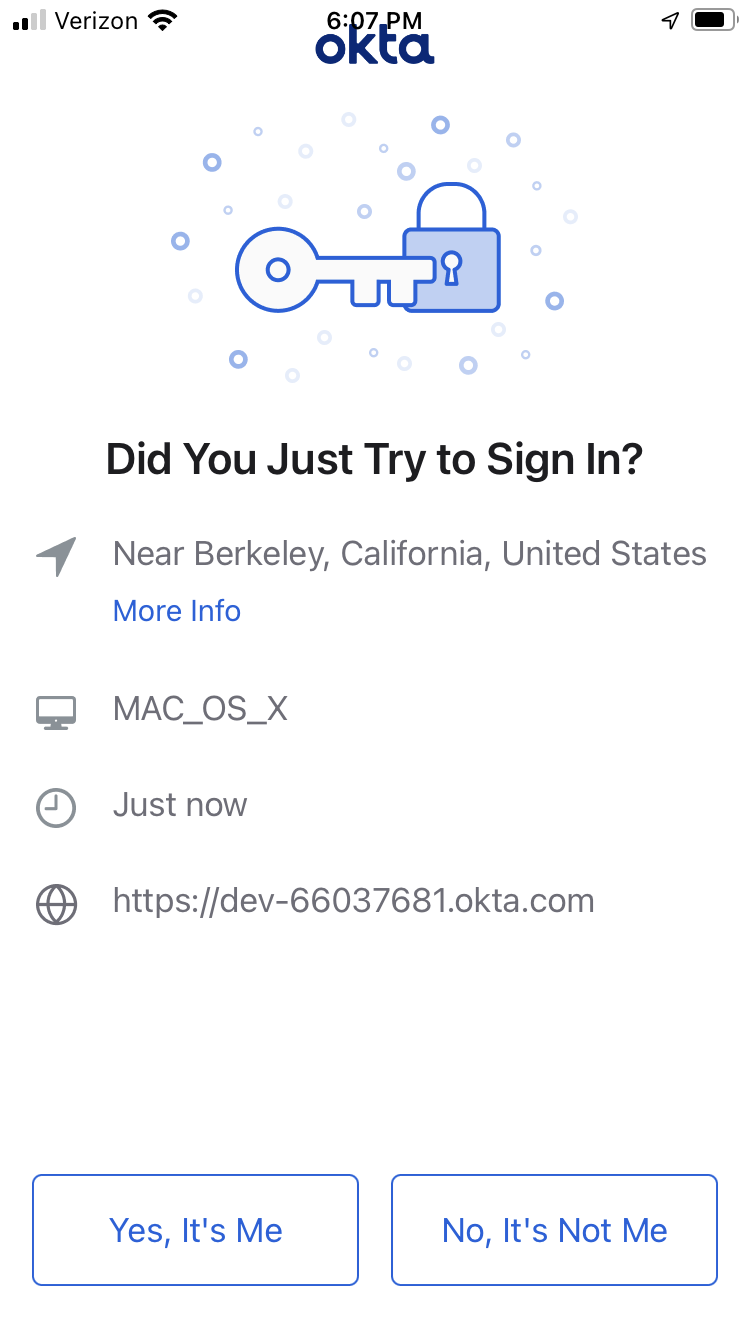
X-Forwarded-For HTTP header.
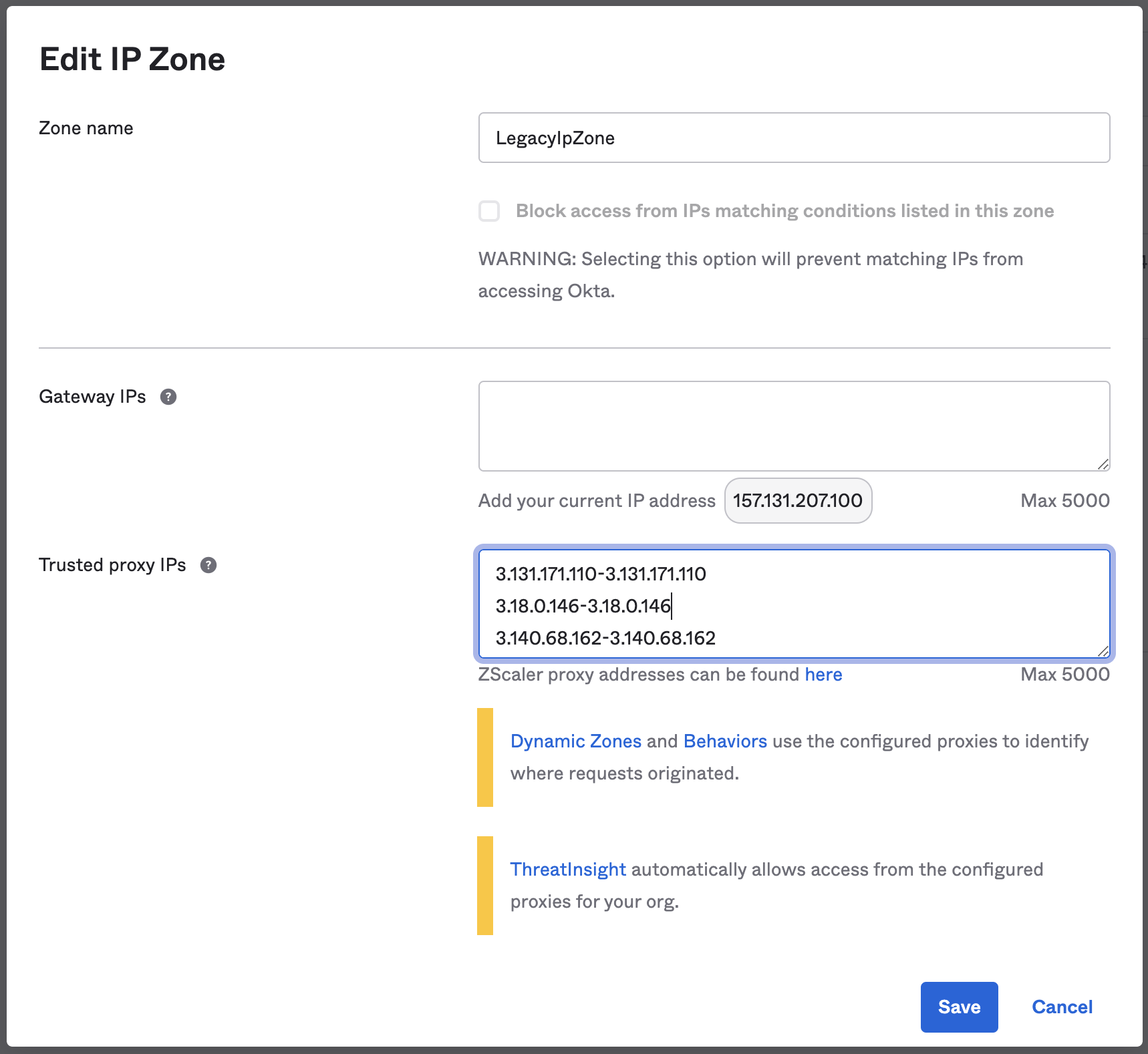
Note: If running Opal self-hosted, please use the public IP ranges for your infrastructure.
Navigate to the Configuration section in Okta:
- Under Security, click Networks.
- Edit the allowlist IP zone.
- Add the IP ranges under Trusted proxy IPs, like so: