Access Rules are available on cloud-hosted Opal and self-hosted Opal versions
1.943.0 and later.
- Provision access based on workplace events (e.g. Joiner, Mover, Leaver)—Opal automatically syncs users and updates access downstream when users onboard, transfer, or leave your IDP or HRIS
- Automate and codify your desired state of identity and access at scale
Requirements
To create and delete Access Rules, you must:- Be an Opal Admin
- Connect Opal to your IDP/HRIS system
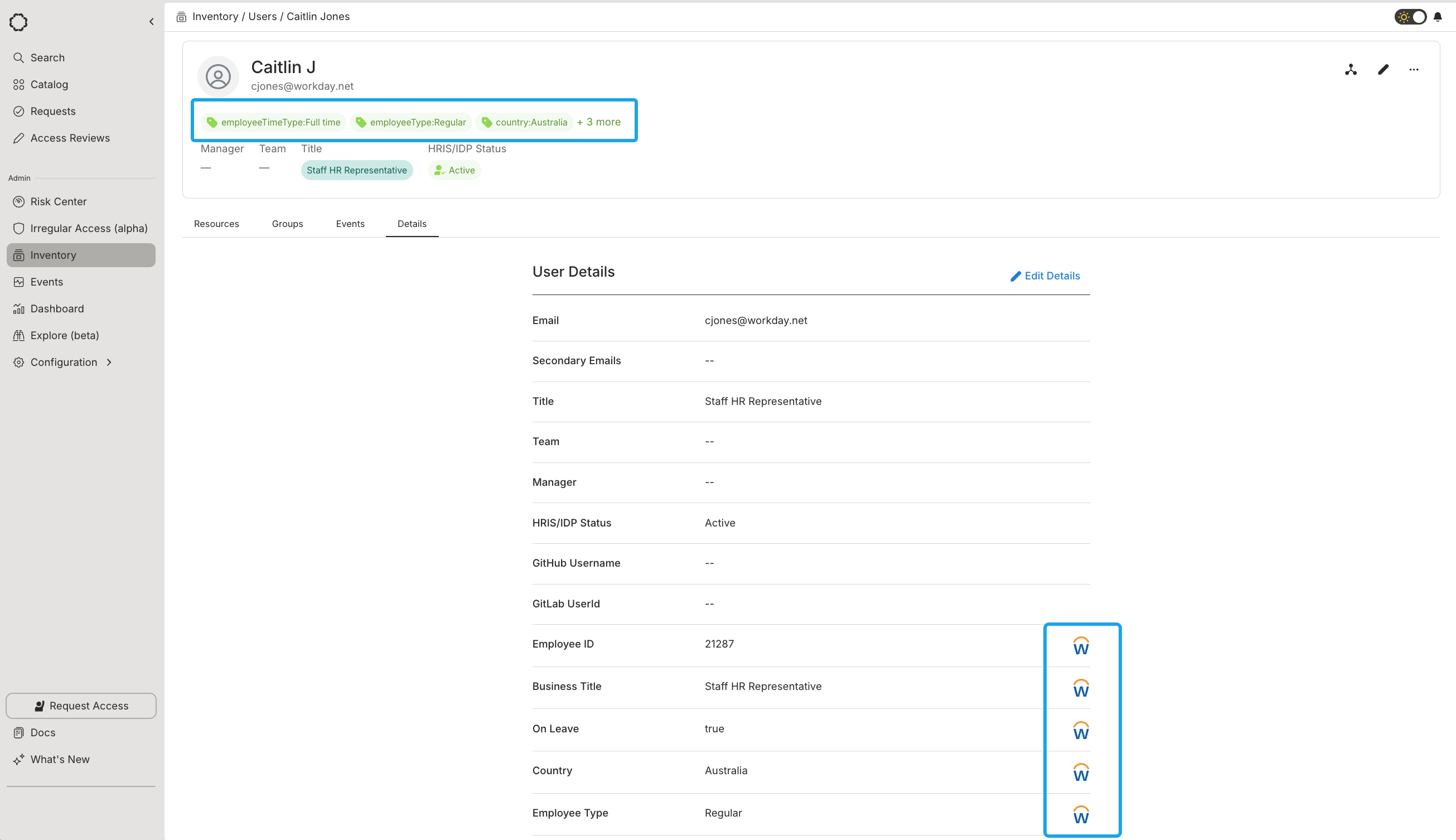
- Import attributes from your IDP/HRIS system as User Tags (custom attributes)
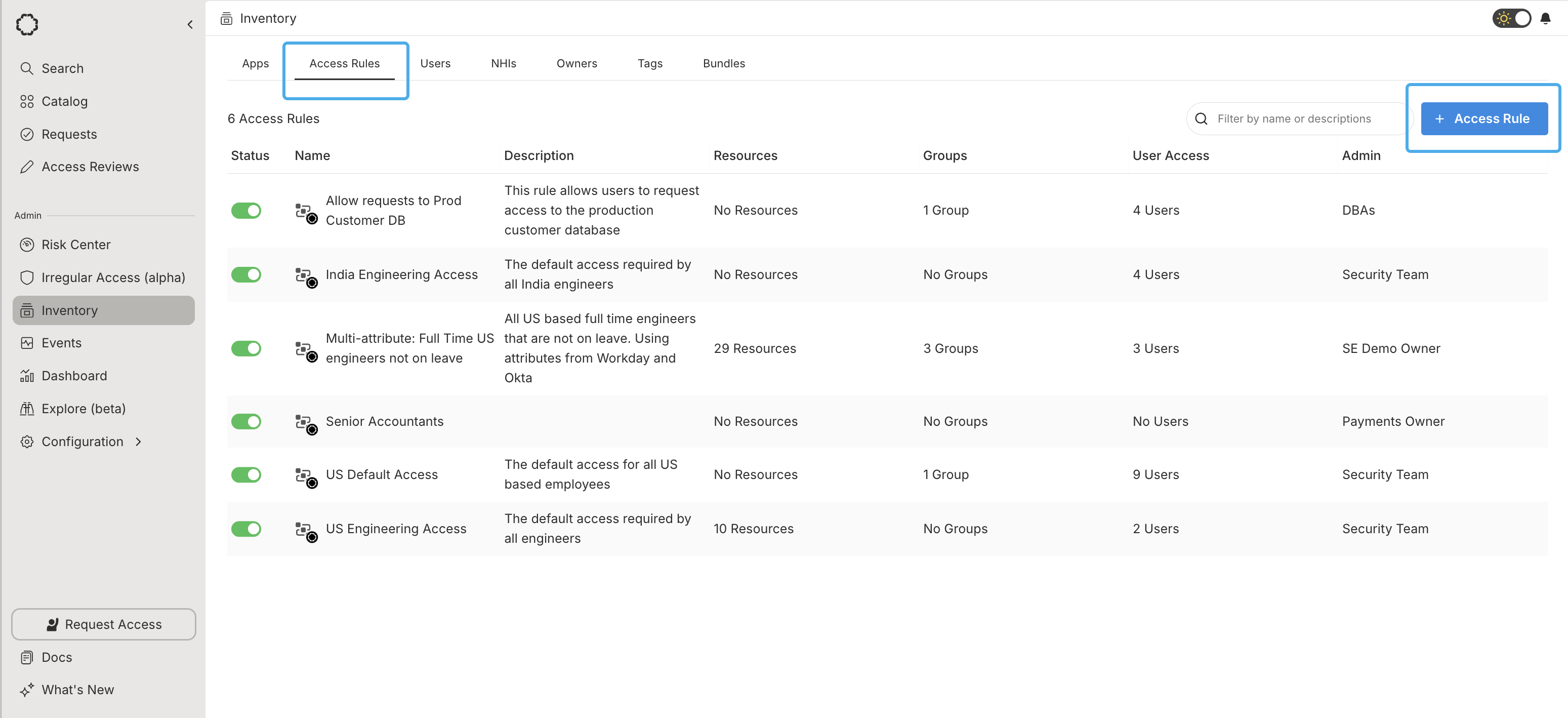
Create Access Rules
Access Rules do not affect access to groups or resources until you’ve
explicitly granted access, so it is
safe to create and modify Access Rules while you determine your ideal
conditions.
Set conditions
Access Rules consist of conditions, which you use to filter a list of users based on tags imported from your IDP. Conditions use the conjunctive normal form, expressed as an AND of ORs. You can exclude users with the Except… clause. The following example filters users to full-time engineers living in the United States. The condition includes users tagged with Country:United States AND (position:Senior Network Engineer OR position:Integration Engineer), and the Except… clause excludes any users tagged with employeeTimeType:PartTime.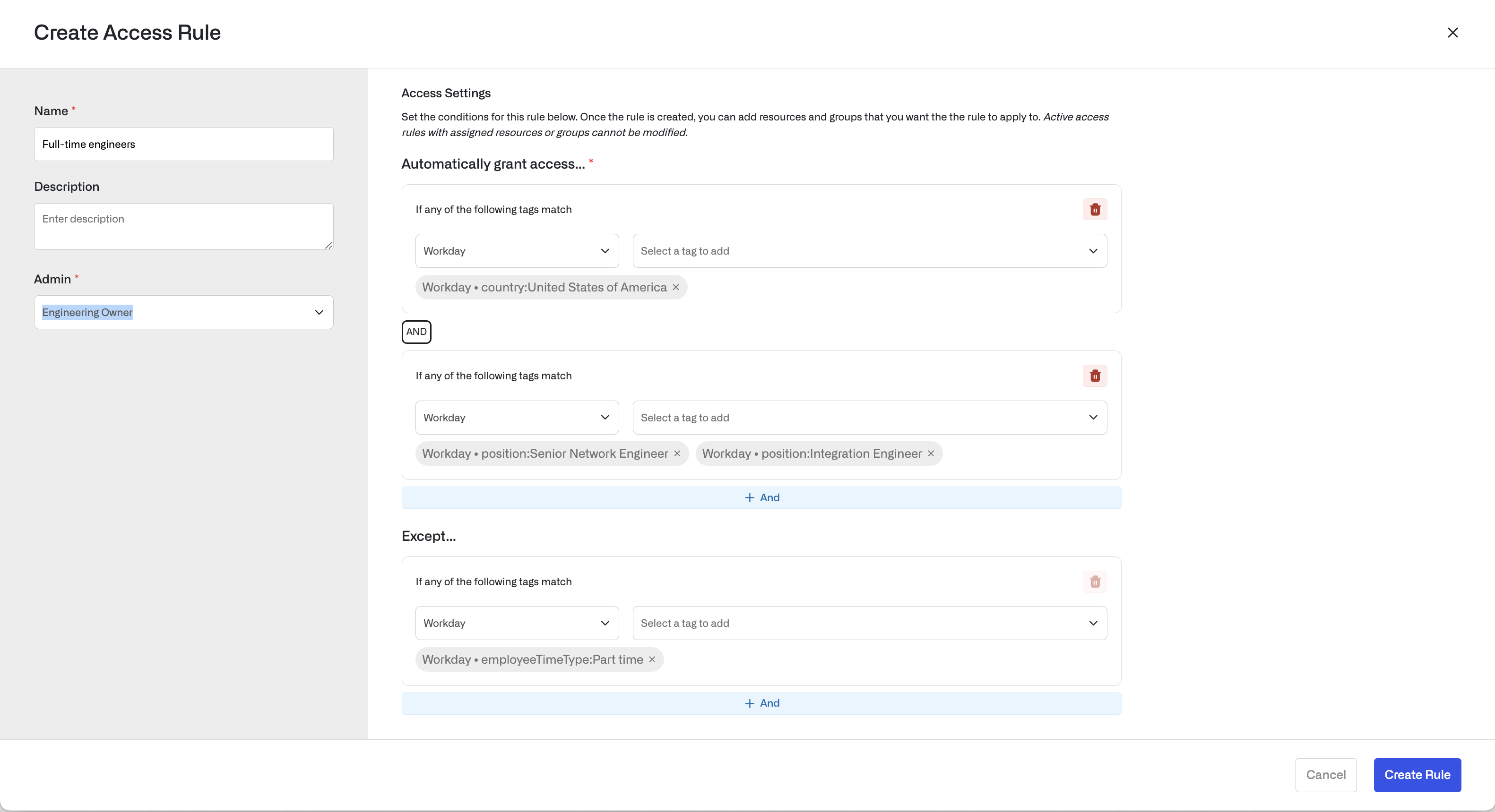
Grant access to groups and resources
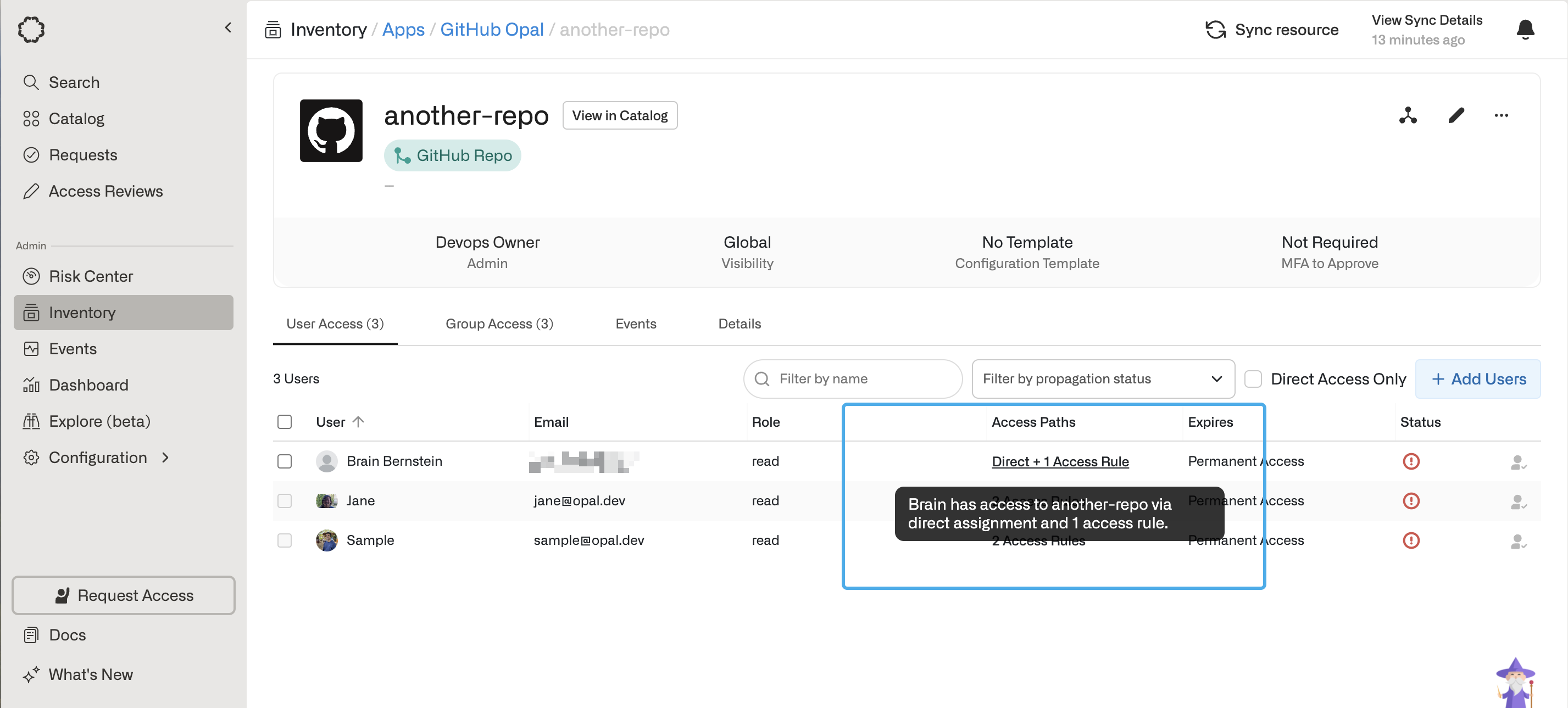
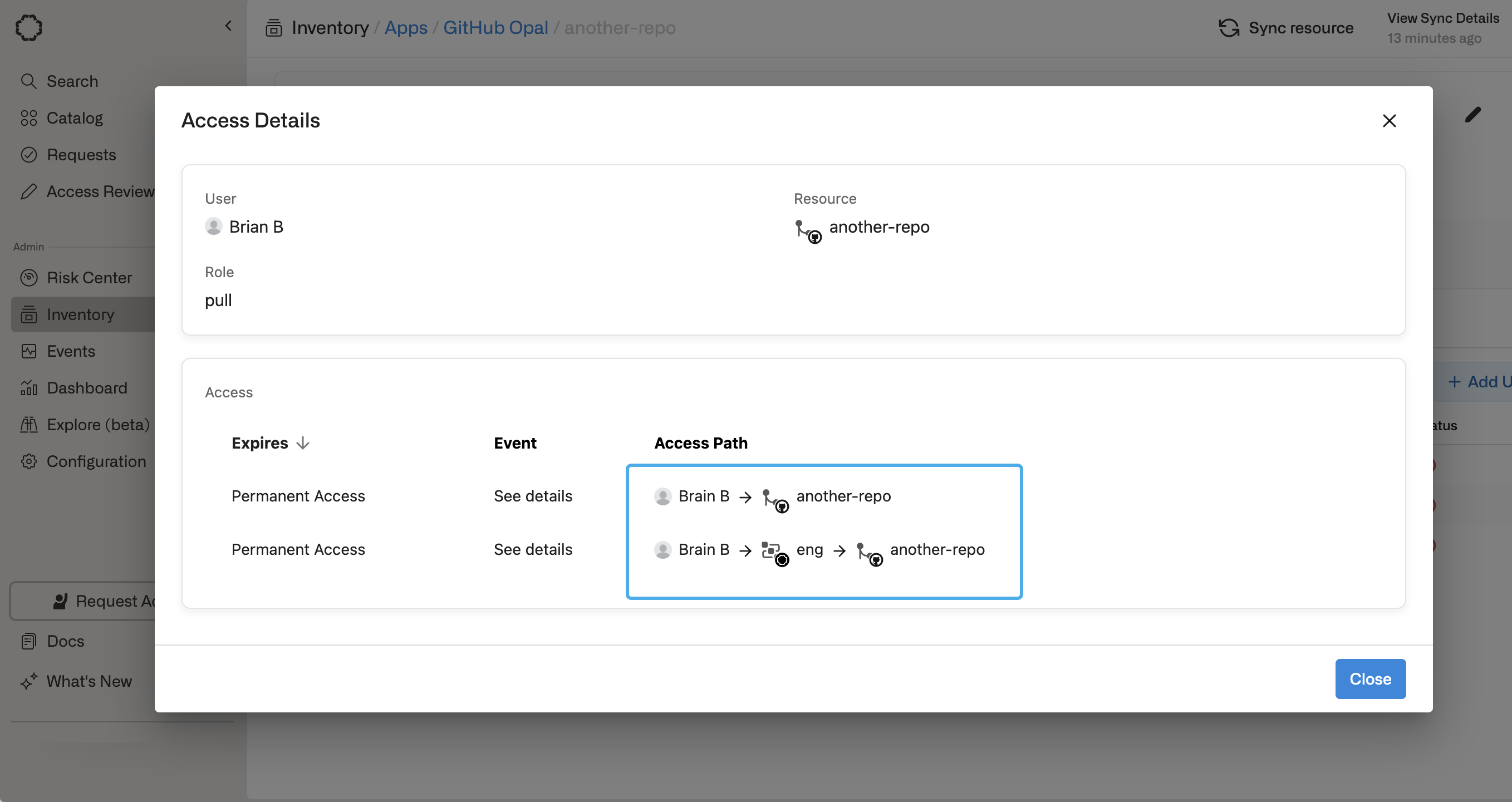
In the Resources tab on your Access Rule, you can grant access to groups and resources as you would for an individual group or user. You can also set the access duration to be indefinite or timebound.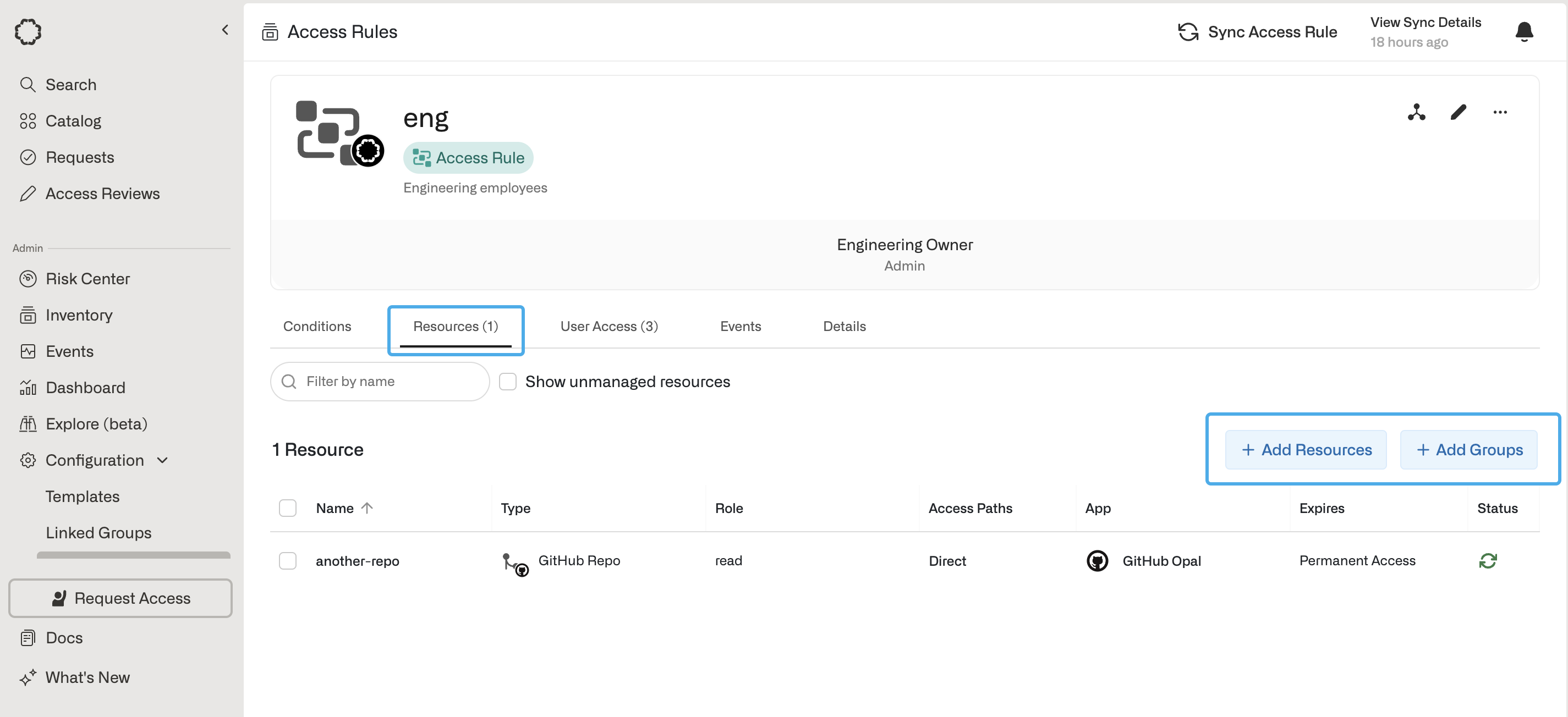
Grant access with Terraform
Use opal_group_resource_list and opal_group_containing_group to assign resources and groups to access rules. Set the access rule ID as thegroup_id.
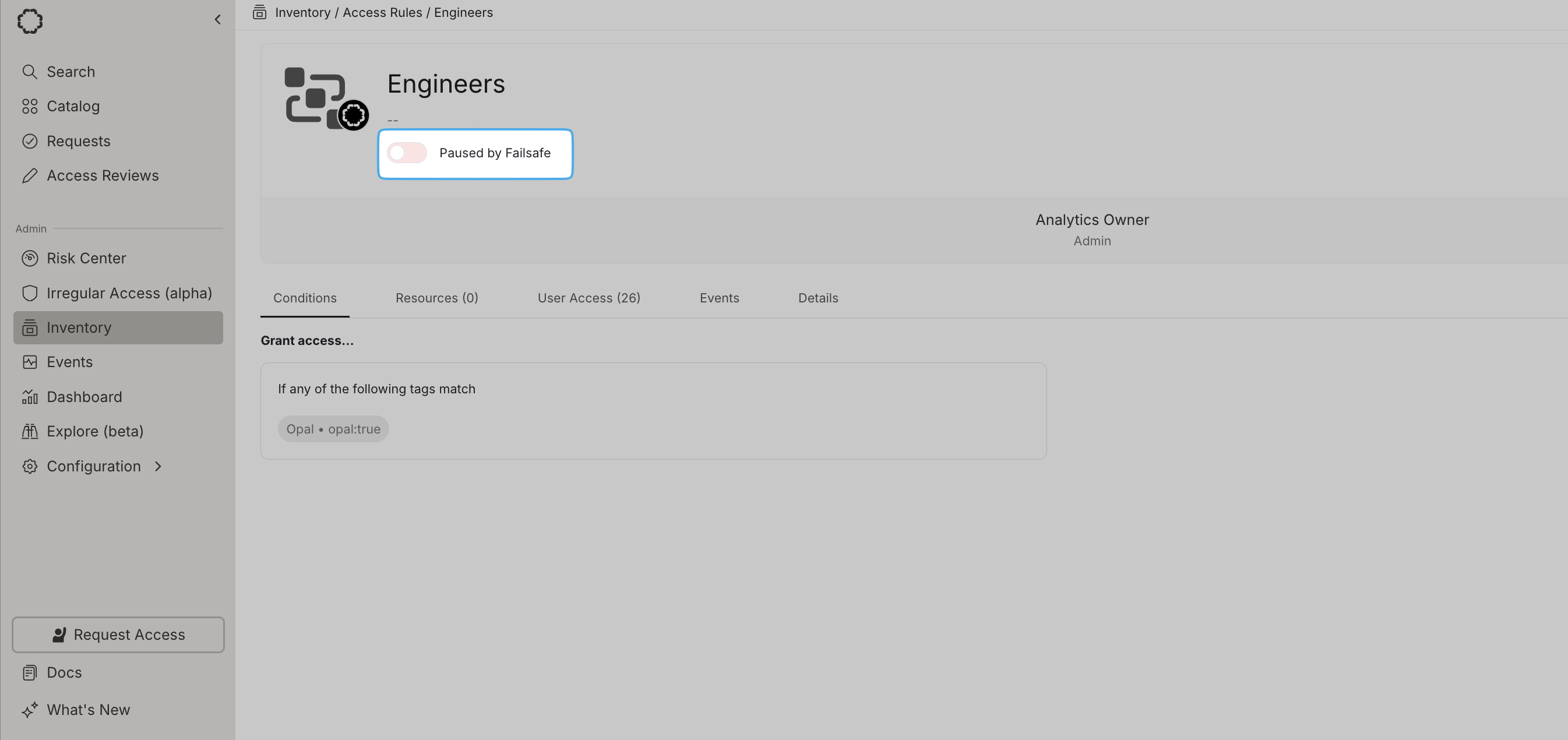
Pause Access Rules
After you create an Access Rule, you can pause it to prevent new users from being added to the rule. Existing users, even if they no longer match the conditions, still have access to any resources or groups granted from the rule. Pause and activate Access Rules by toggling the Status column, either on the Access Rules page or from the detail page.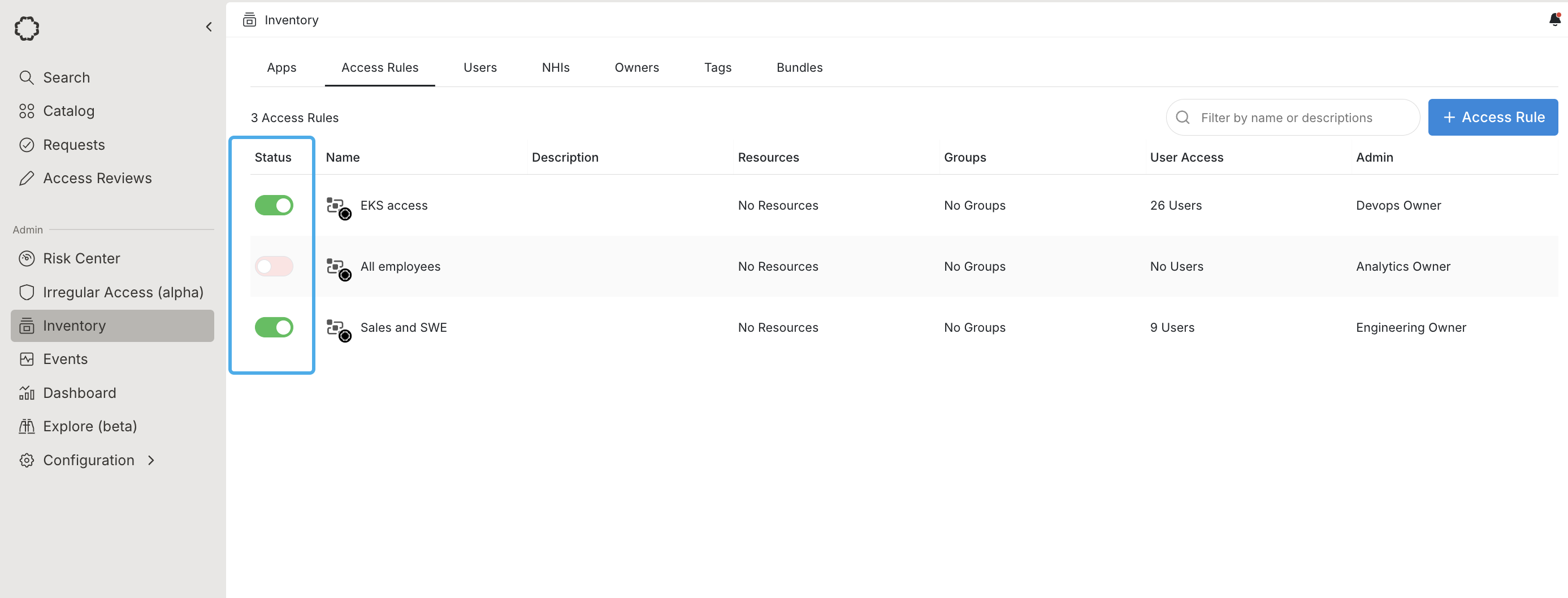
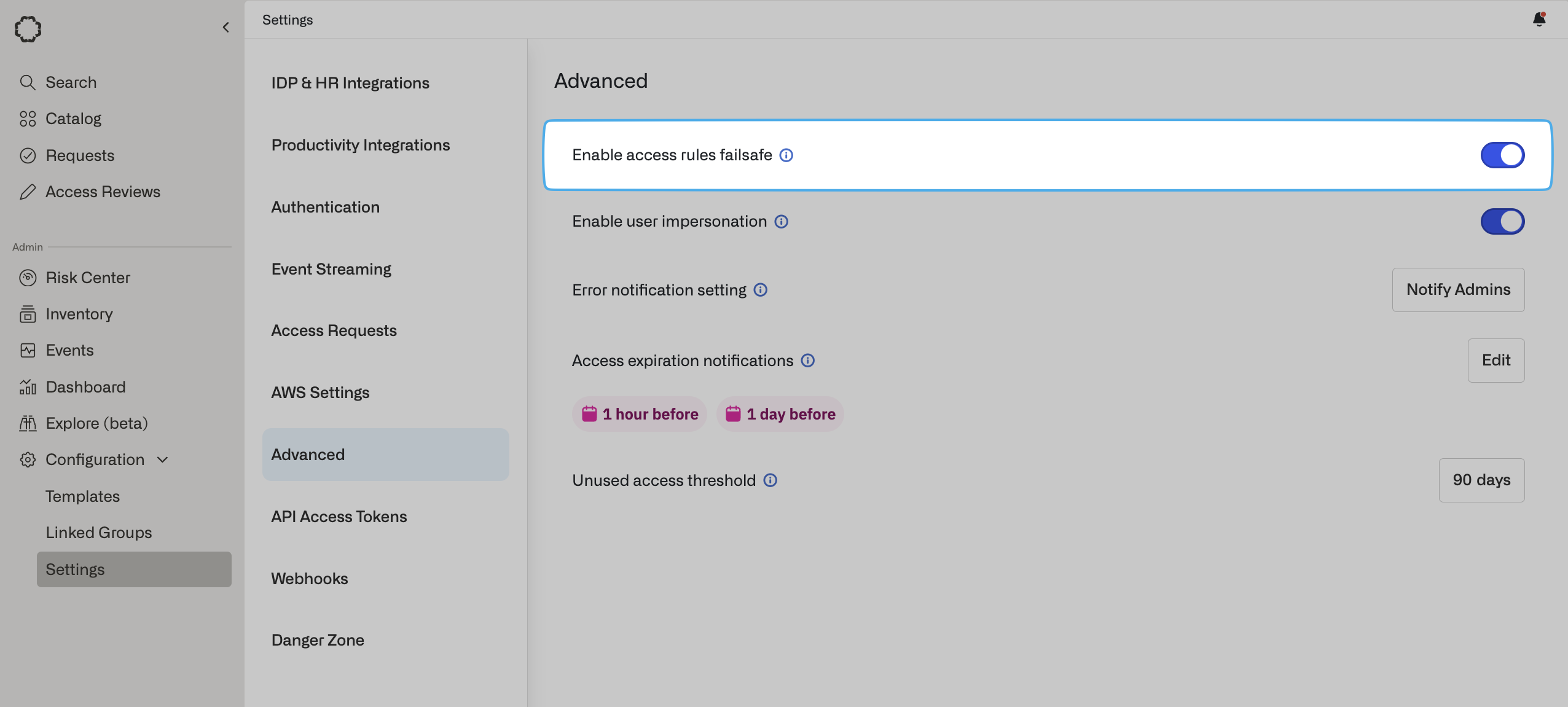
Enable failsafe functionality
Failsafe functionality is available on Opal cloud and self-hosted Opal
versions [1.929.0] and later.
Test conditions for given users
To test whether a given user will be included in an access rule and granted access to its resources and groups, enter a user from the Conditions tab on an existing rule. This can be especially useful for debugging.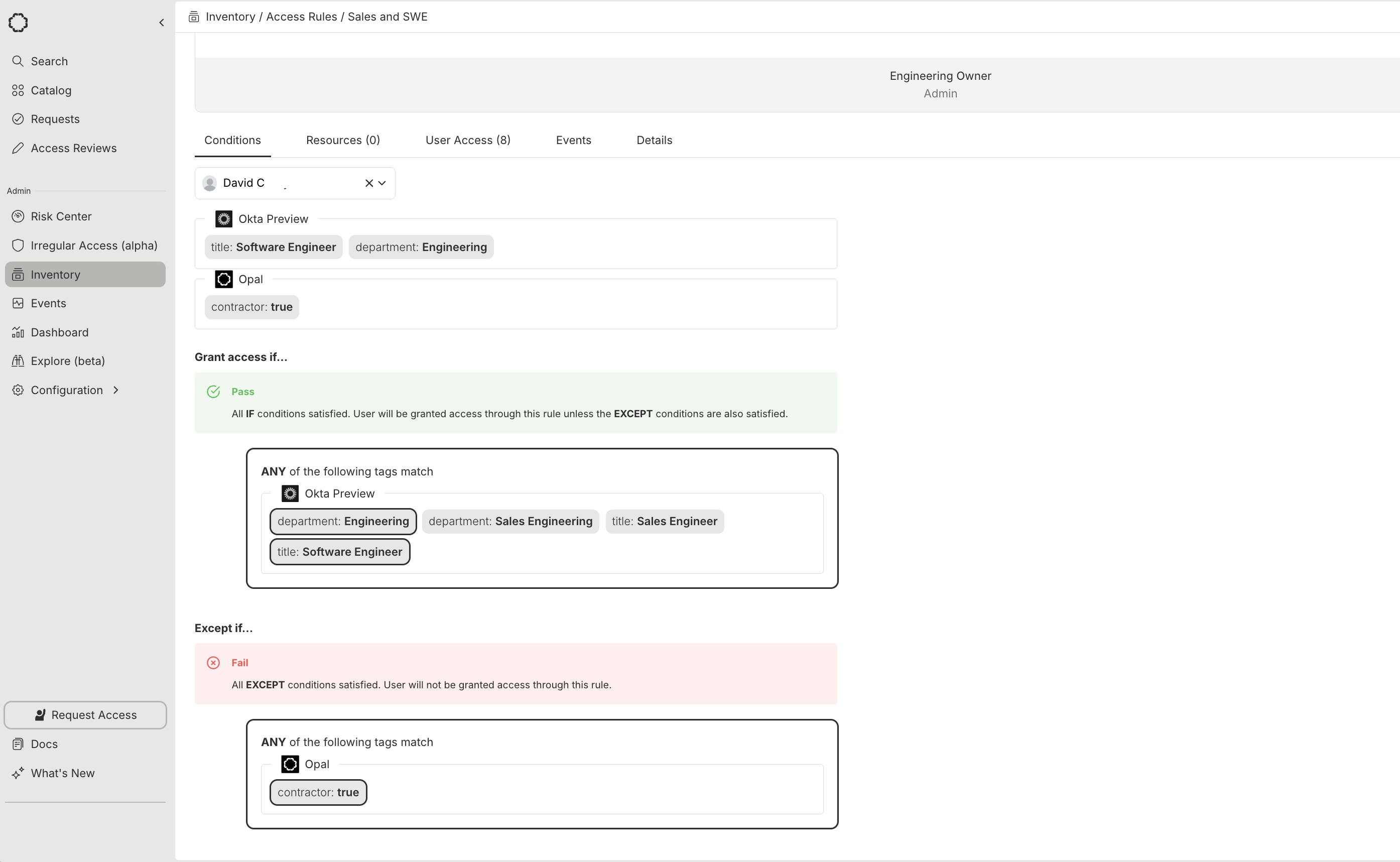
Remove Access Rules
To remove an Access Rule, go to the detail page for the Access Rule, select …, then Remove from Opal. Deleting an Access Rule does not automatically revoke access from remote systems, even if access was granted from the rule. To remove access granted by Opal, first delete all resources and groups from the rule, then remove the rule.Review resources associated with Access Rules
To review what resources an Access Rule grants its matching users access to, you can create a User Access Review, scope it to the desired Access Rules by selecting Add entity > then searching for the Access Rule under the Groups dropdown. You can also review resources across multiple Access Rules by selecting Add entity type > then searching for the Access Rule under the Group types dropdown.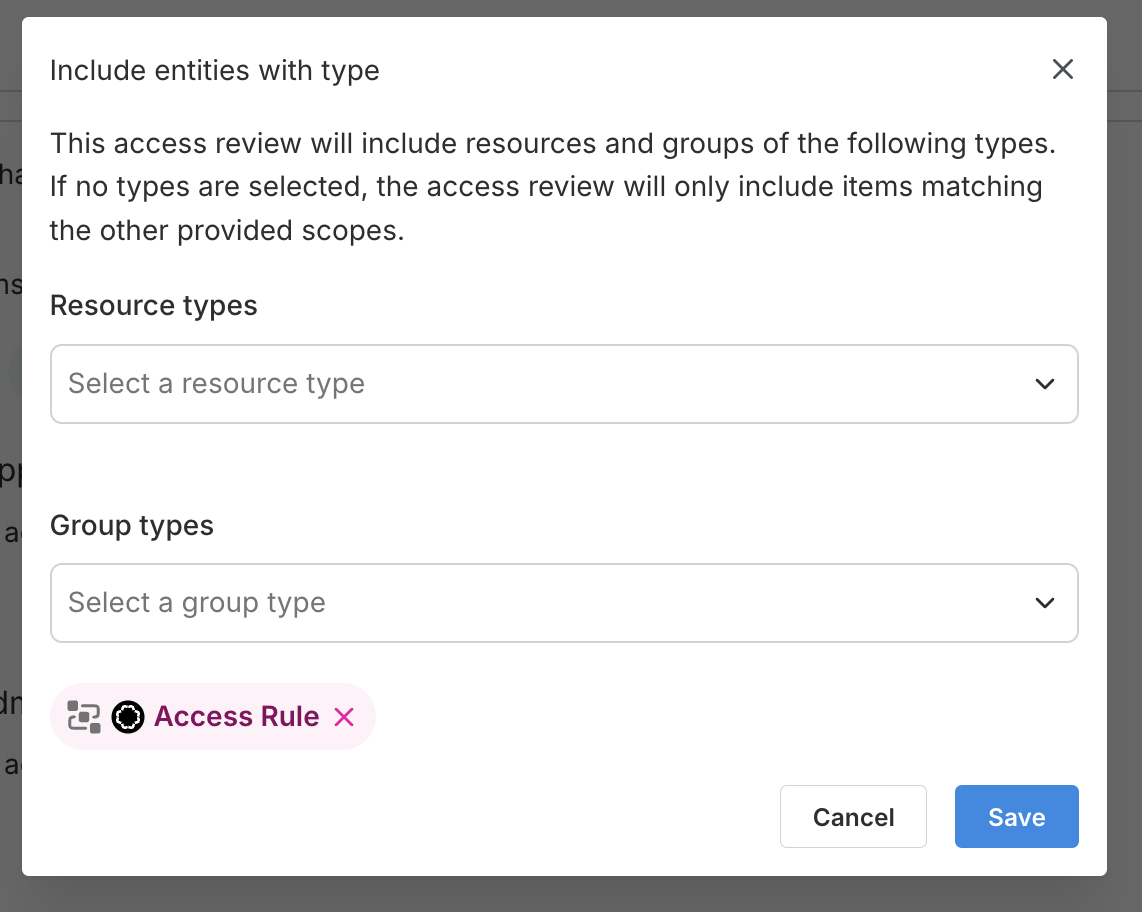
Configure access requests based on Access Rule membership
You can also use Access Rules to dynamically enforce which users can request access to resources based on attributes. On the resource, navigate to Edit > Request Configuration > Add a New Configuration > and under Requesting Groups, select the Access Rule.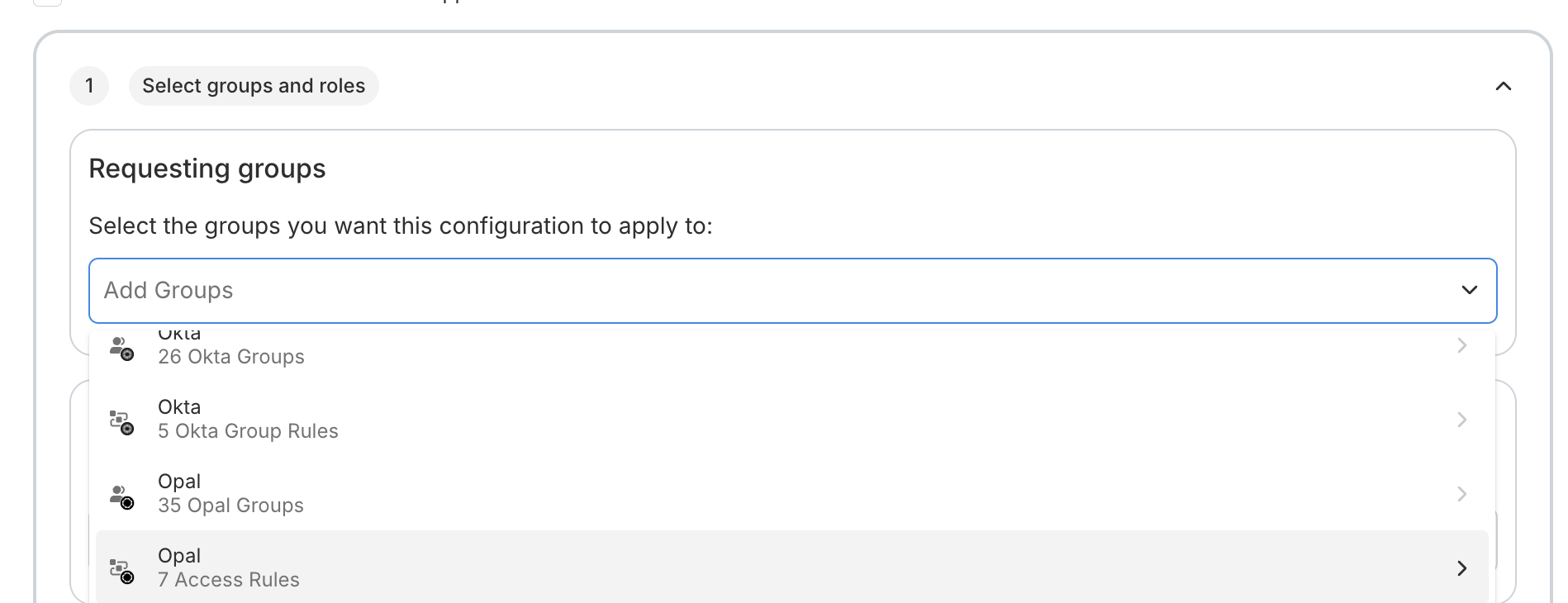
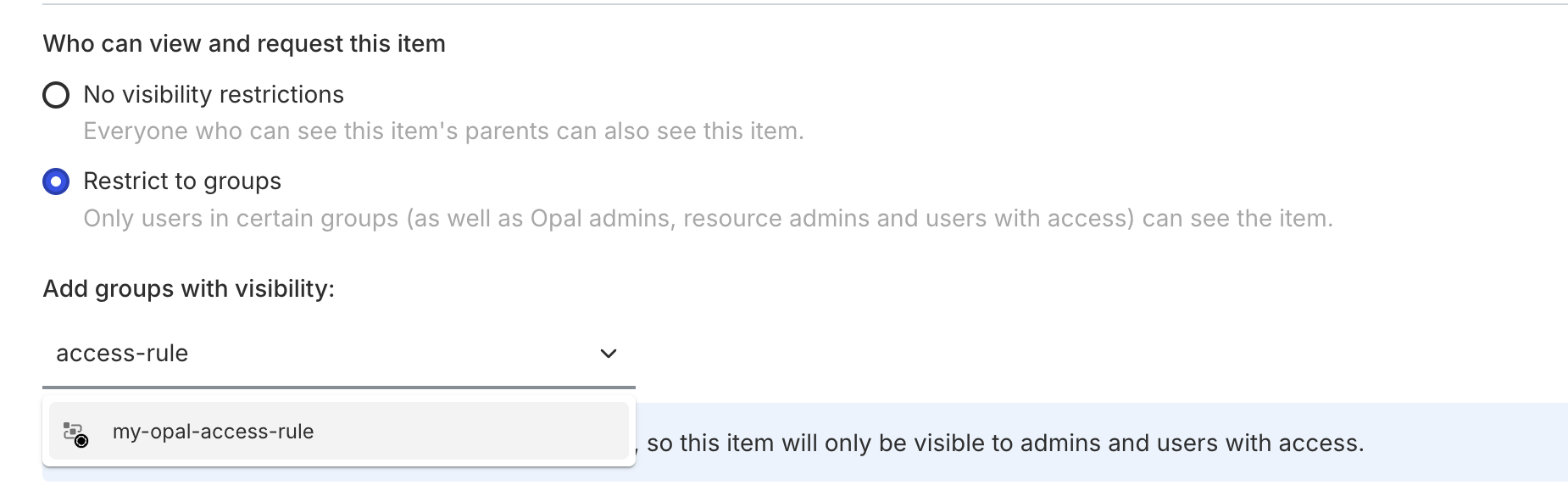
Configure visibility based on Access Rule membership
You can also use Access Rules to dynamically enforce which users can view resources based on attributes. On the resource, navigate to Edit > Restrict to groups > Add groups with visibility: > then select the Access Rule.