You can use OpenID Connect (OIDC) to authenticate users for actions that require additional authentication, configured at the resource level. This includes requesting access, approving an access request, and/or connecting to a session.
OIDC Provider Setup
Prerequisite: You must register a new OIDC Provider with your IDP.
https://{YOUR_OPAL_BASE_URL}/callback/oidc, substituting in your Opal base URL (e.g. https://app.opal.dev/callback/oidc) .For more information about obtaining these credentials, refer to your IdP’s documentation: Okta OIDC docs, Google OIDC docs
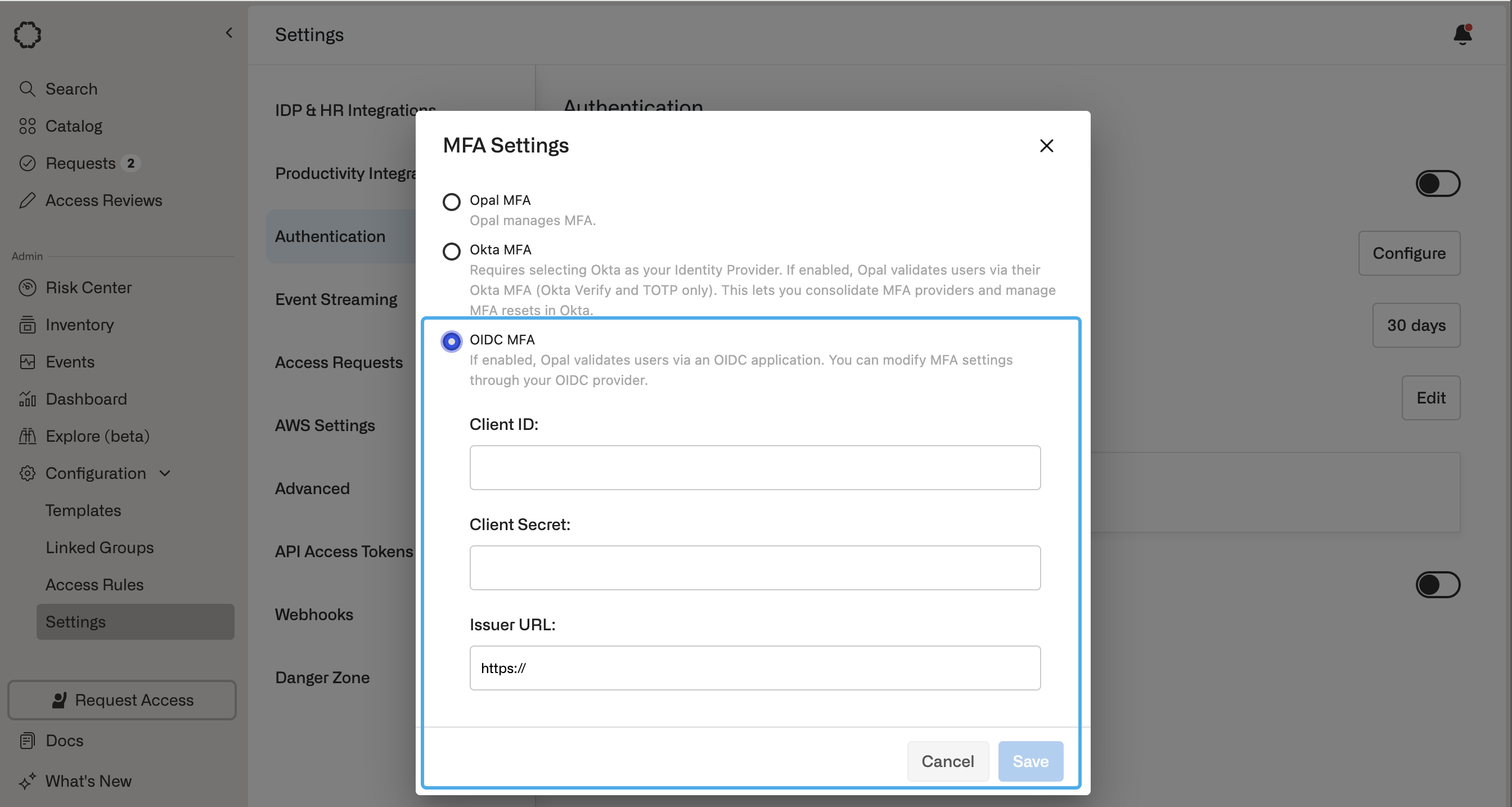
When registering your OIDC provider with Opal, you must have the following information available: Client ID, Client Secret, and Issuer URL.
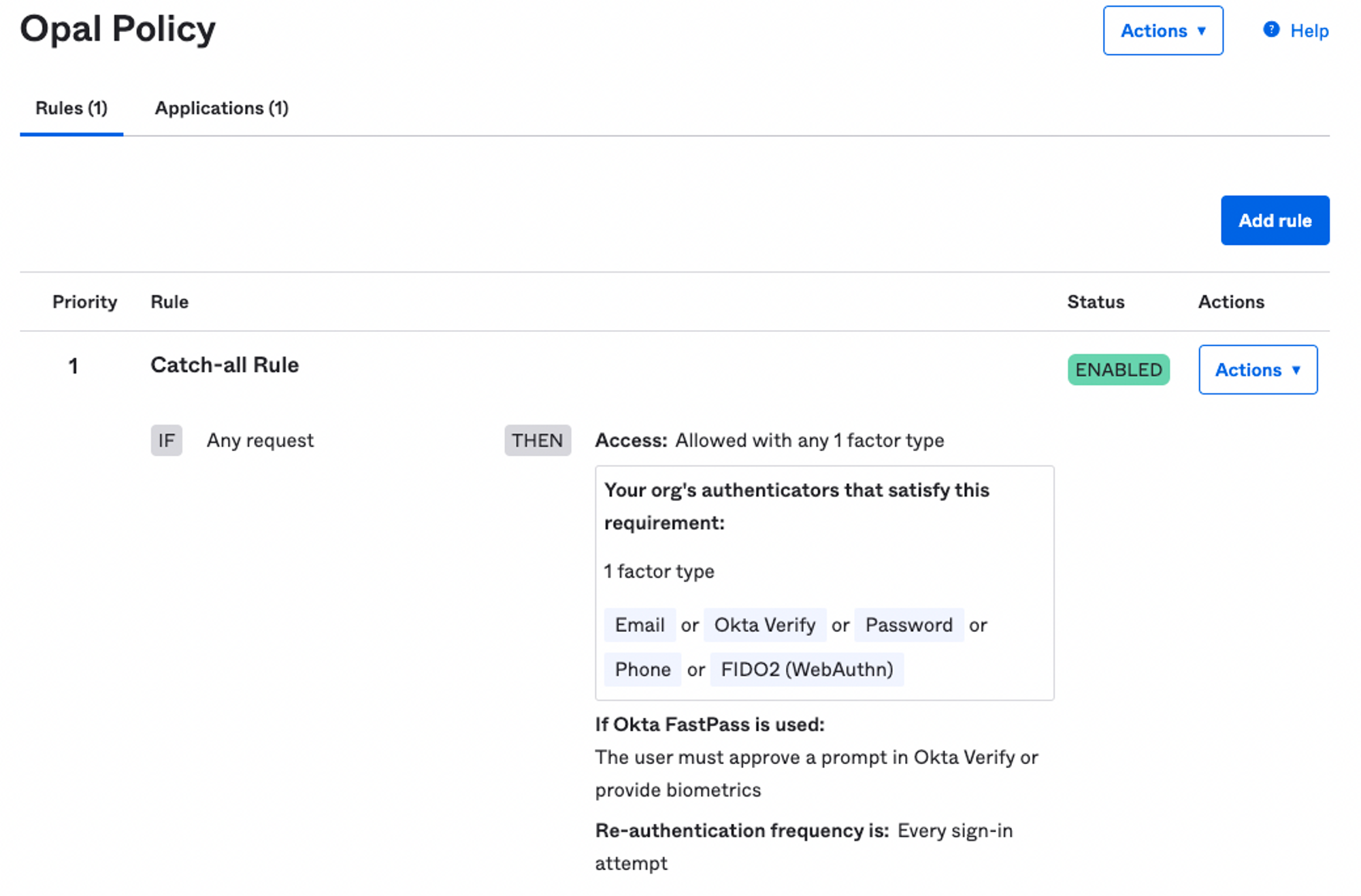
The OIDC provider must be configured to require MFA for every sign-in attempt. Password authentication is not required.
- In Opal, go to Configuration > Settings in the left sidebar.
- Click Authentication, then MFA settings for gated Opal Actions. Click Configure.
- Select OIDC MFA and fill in the Client ID, Client Secret, and Issuer URL from your IdP.