- Opal logins: you can configure Opal to require MFA when a user logs in.
- Opal actions: you configure resources in Opal to require MFA for requesting access, approving an access request, and/or connecting to a session.
Enable MFA for Opal logins
Toggle the Require Opal MFA for logins setting to enable Opal-managed MFA.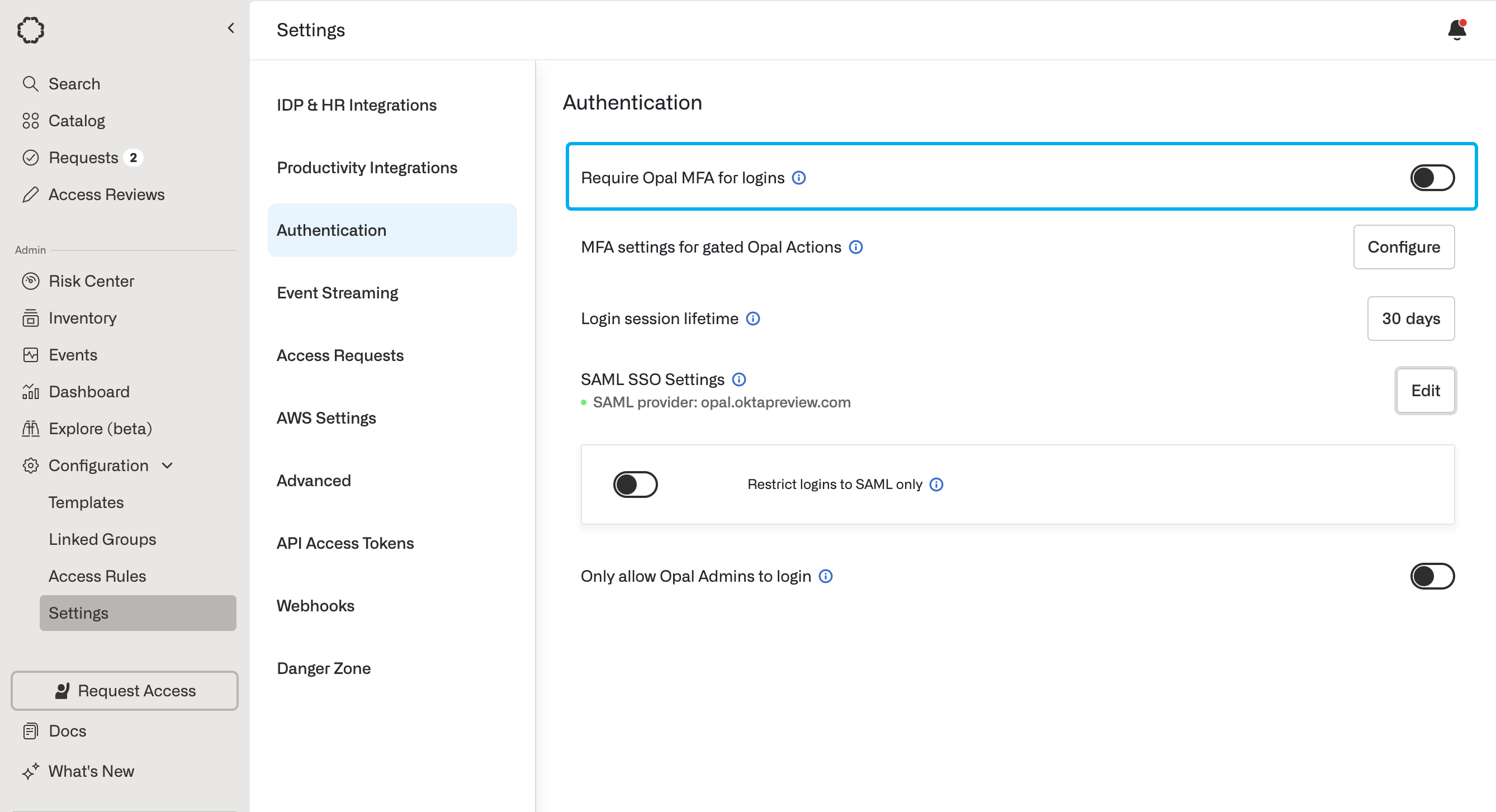
Enable MFA for Opal actions
MFA for Opal actions can be toggled on a per-action, per-resource level. Edit your resource to enable MFA.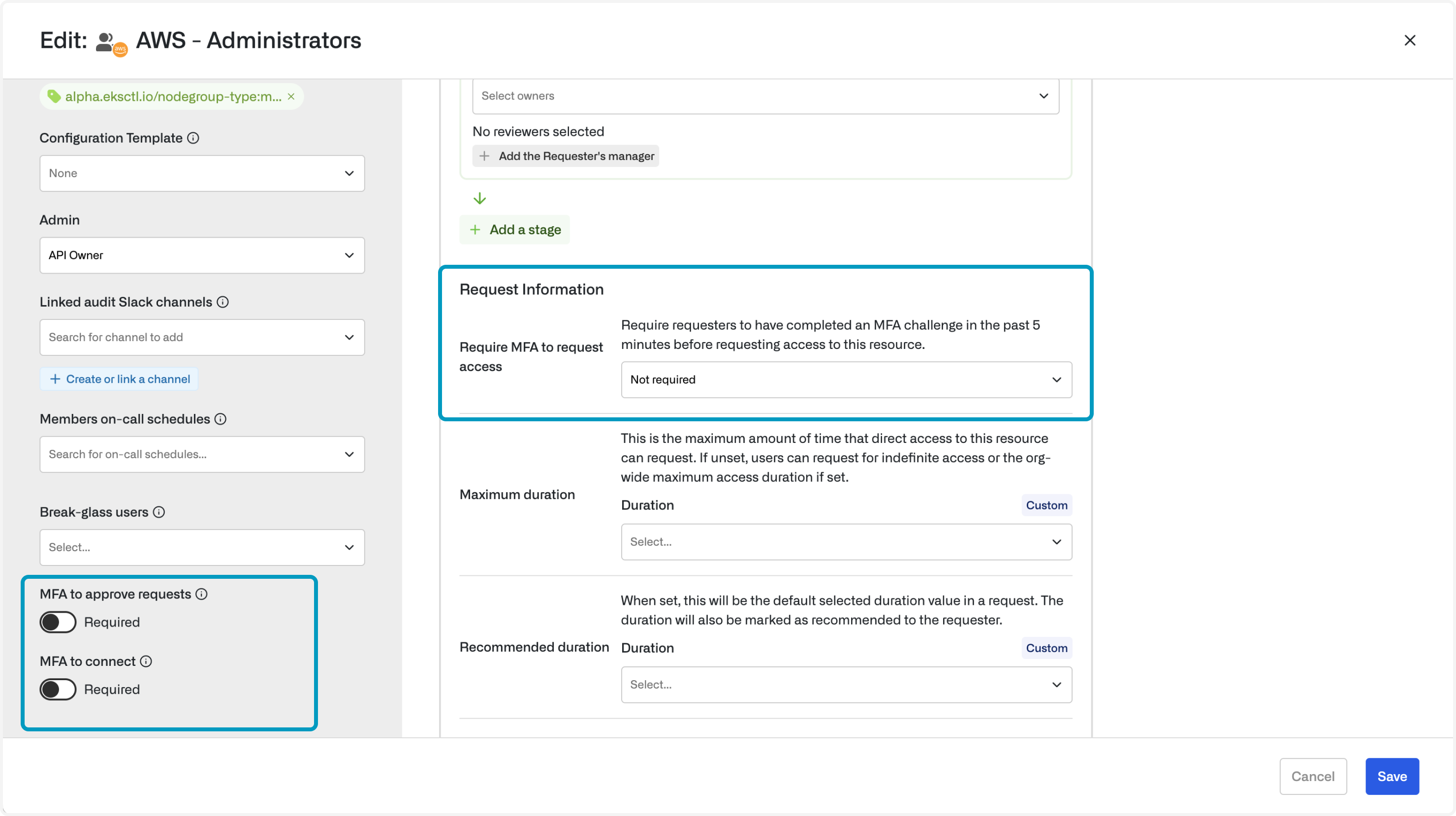
- Opal managed MFA: Users can register their MFA devices through Opal.
- Okta-managed MFA [Legacy]: Okta Verify and TOTP. Users may only use these two factors for MFA.
- OIDC MFA: Opal supports any OIDC provider, including Okta and Azure, as a MFA solution. Once configured, users will be able to use any MFA method that your OIDC provider supports, including WebAuthn (Yubikey, TouchID, etc.) and TOTP.
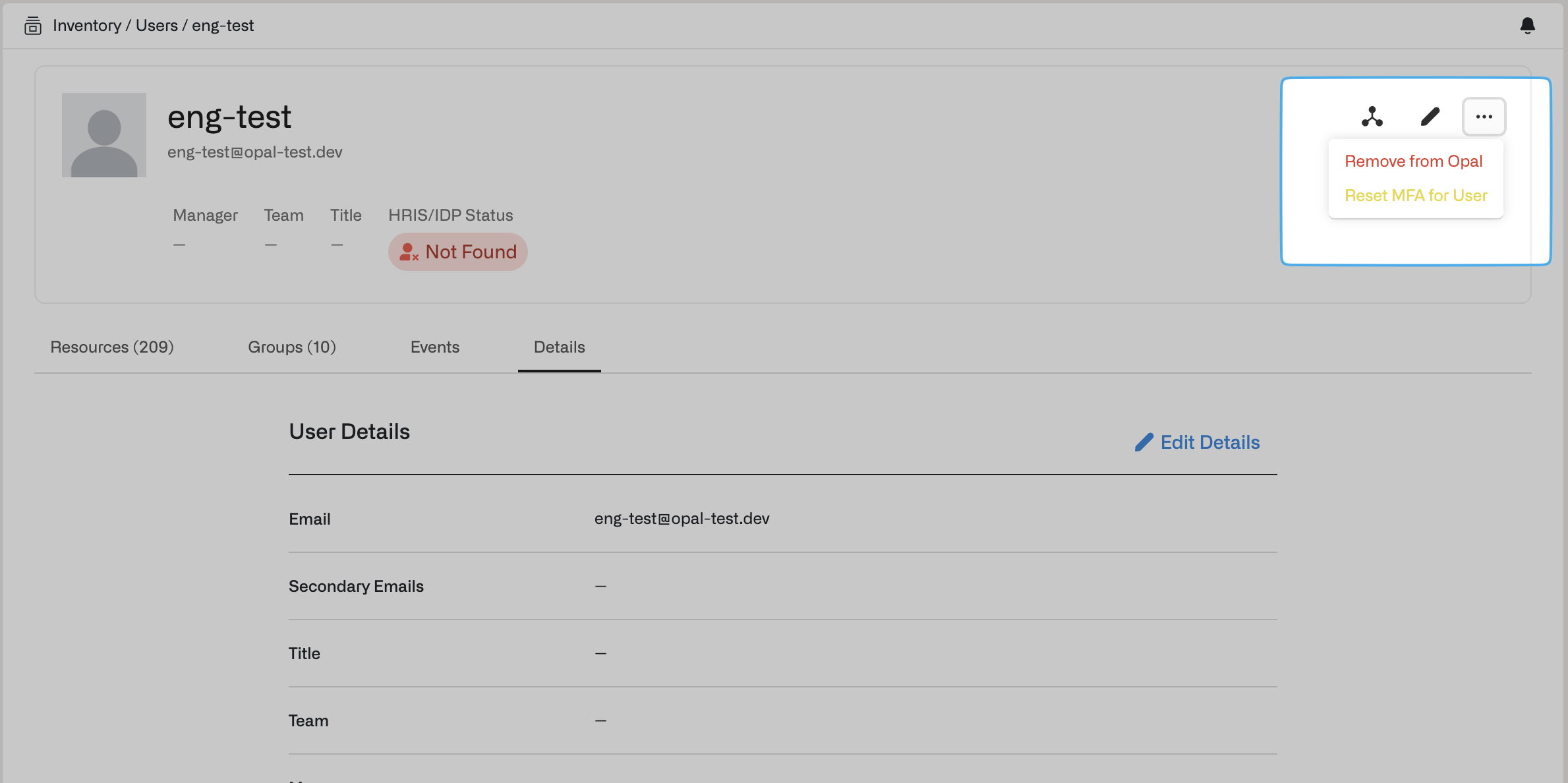
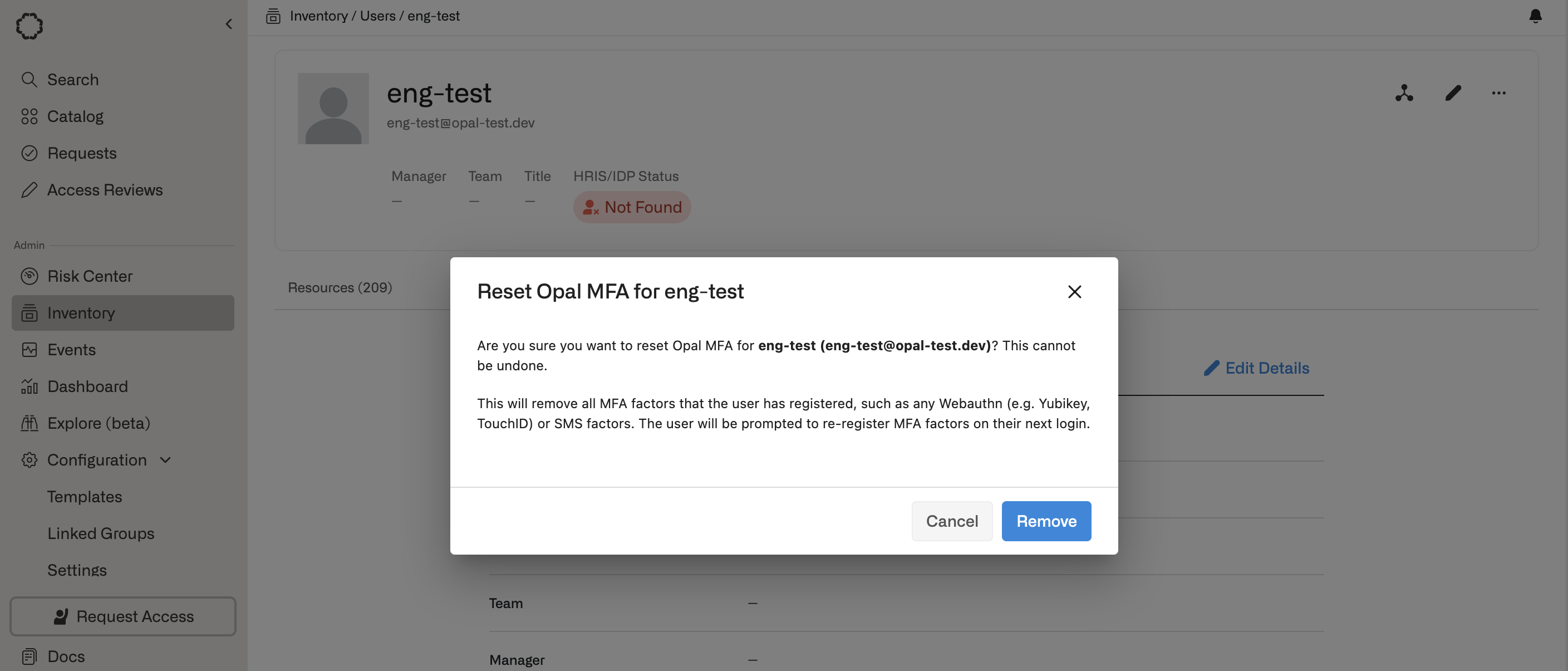
Reset MFA for users
To reset MFA for an individual user, go to the Inventory > Users tab, then find the user detail page. Select the … dropdown on the upper right, then Reset MFA for User.