Admin Workflows
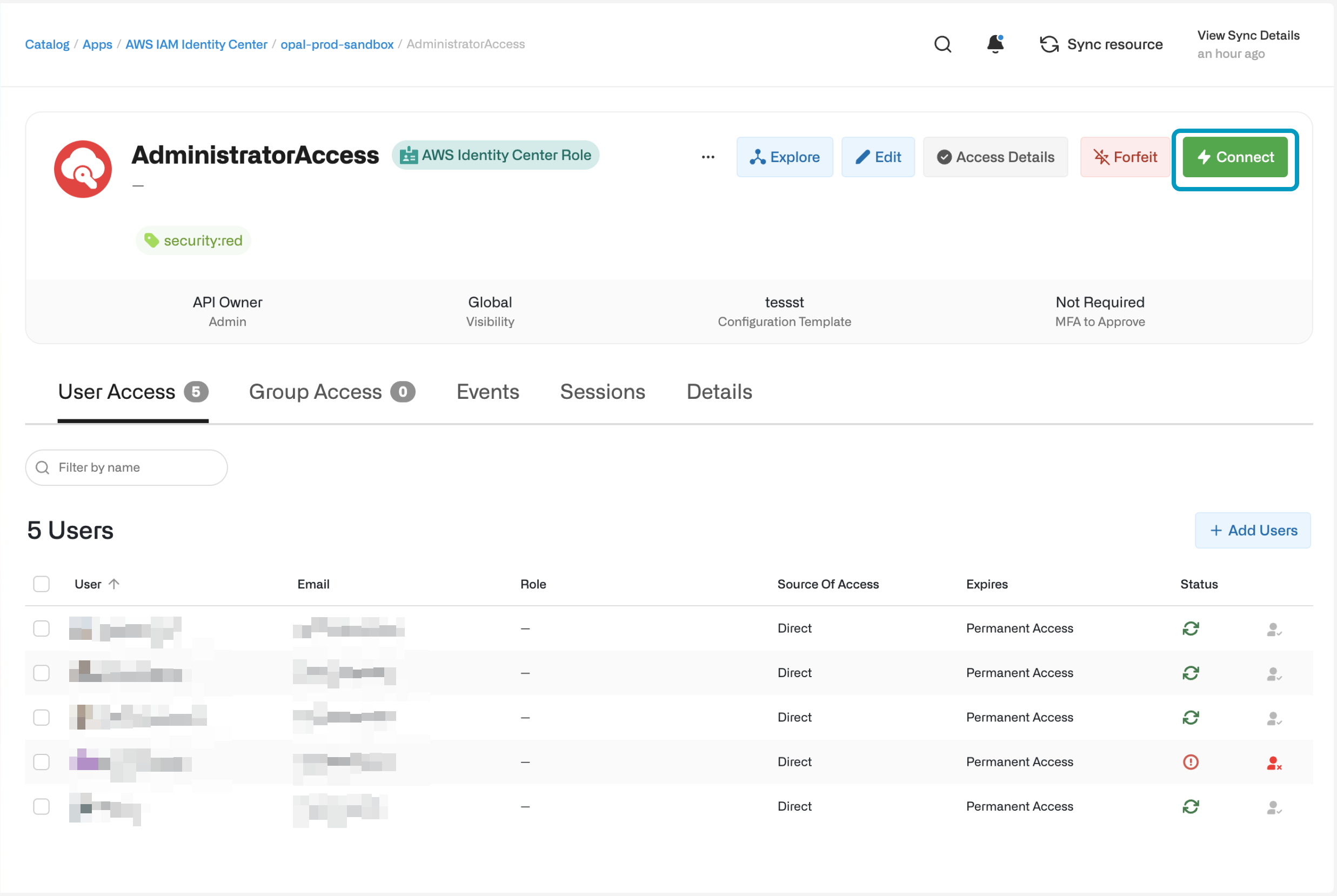
After you’ve created and synchronized the app, you should see that your AWS accounts are populated under the Resources tab. Additionally, you should see that each permission set has a resource nested under every AWS account, regardless of whether that permission set is already provisioned to some users in that account. Because this Opal resource more accurately represents the AWS-managed role that would be in that account instead of the actual permission set, the resource is referred to as an “AWS IAM Identity Center Role”.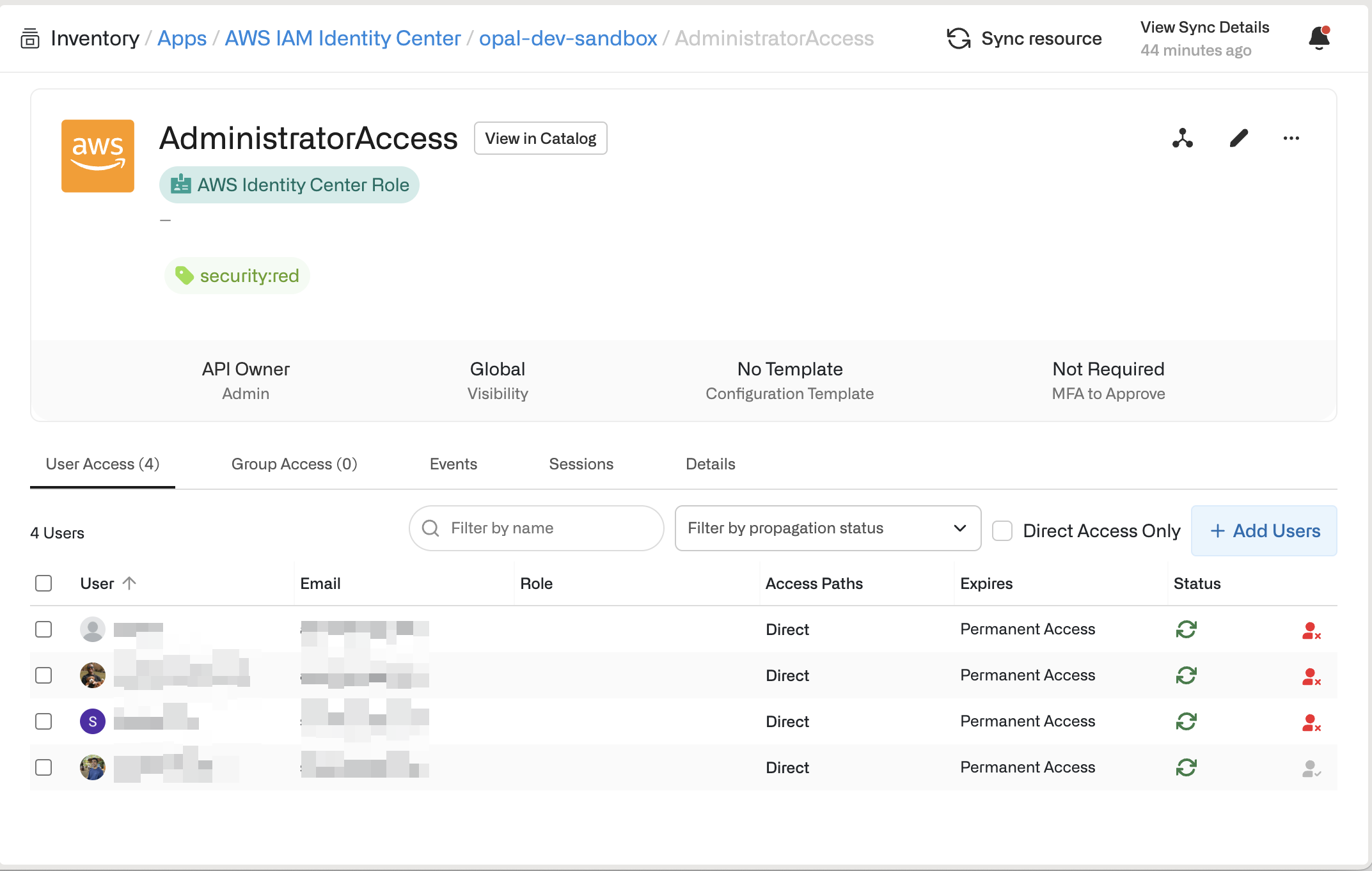
If you use an external IdP source to provision your IAM Identity Center groups, Opal may be unable to synchronize group memberships between IAM Identity Center and the IdP.For Okta, IAM Identity Center group memberships do not automatically refresh when another party updates them. In this case, we recommend only updating user-to-group relationships in Okta and group-to-permission-set relationships in Opal’s IAM Identity Center app to avoid inconsistencies.
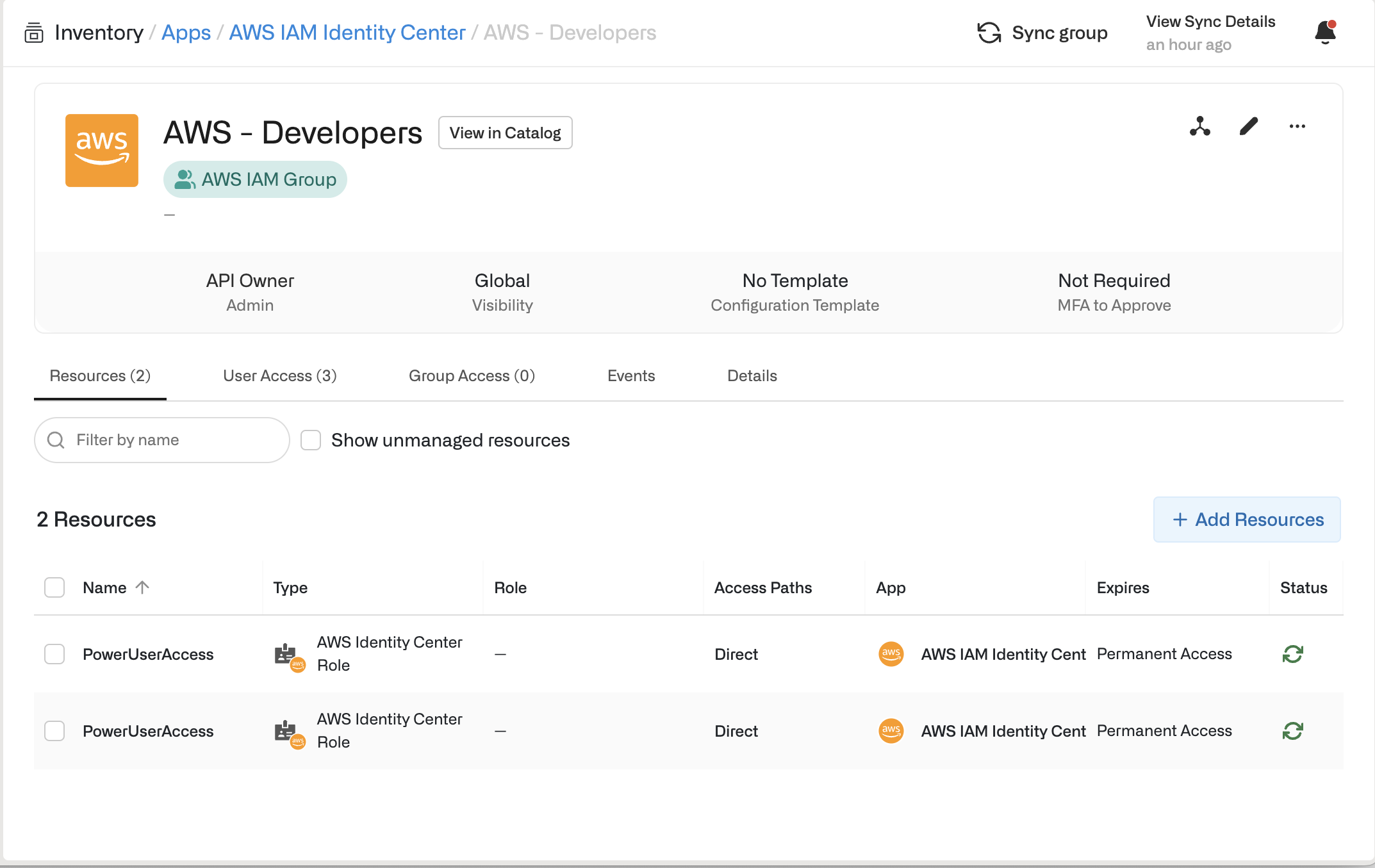
Scoping down sensitive access
Opal automatically creates a resource for each of your permission sets under every AWS account, but you may have some permission sets with particularly sensitive permissions that you want to hide from being requested. There are a couple of ways to achieve this:- You can adjust the visibility setting for the IAM Identity Center Role to be one or many privileged groups. If you do this, then only the members in those groups can view or request this role.
- You can adjust the visibility setting for the parent account, which will also apply to any permission sets nested underneath it. Note accounts can only be set to “Global” or “Admin Only” visibility. By setting the latter, it also makes all IAM Identity Center Roles under the account “Admin Only” and hide it even from users with access.
End User Workflows
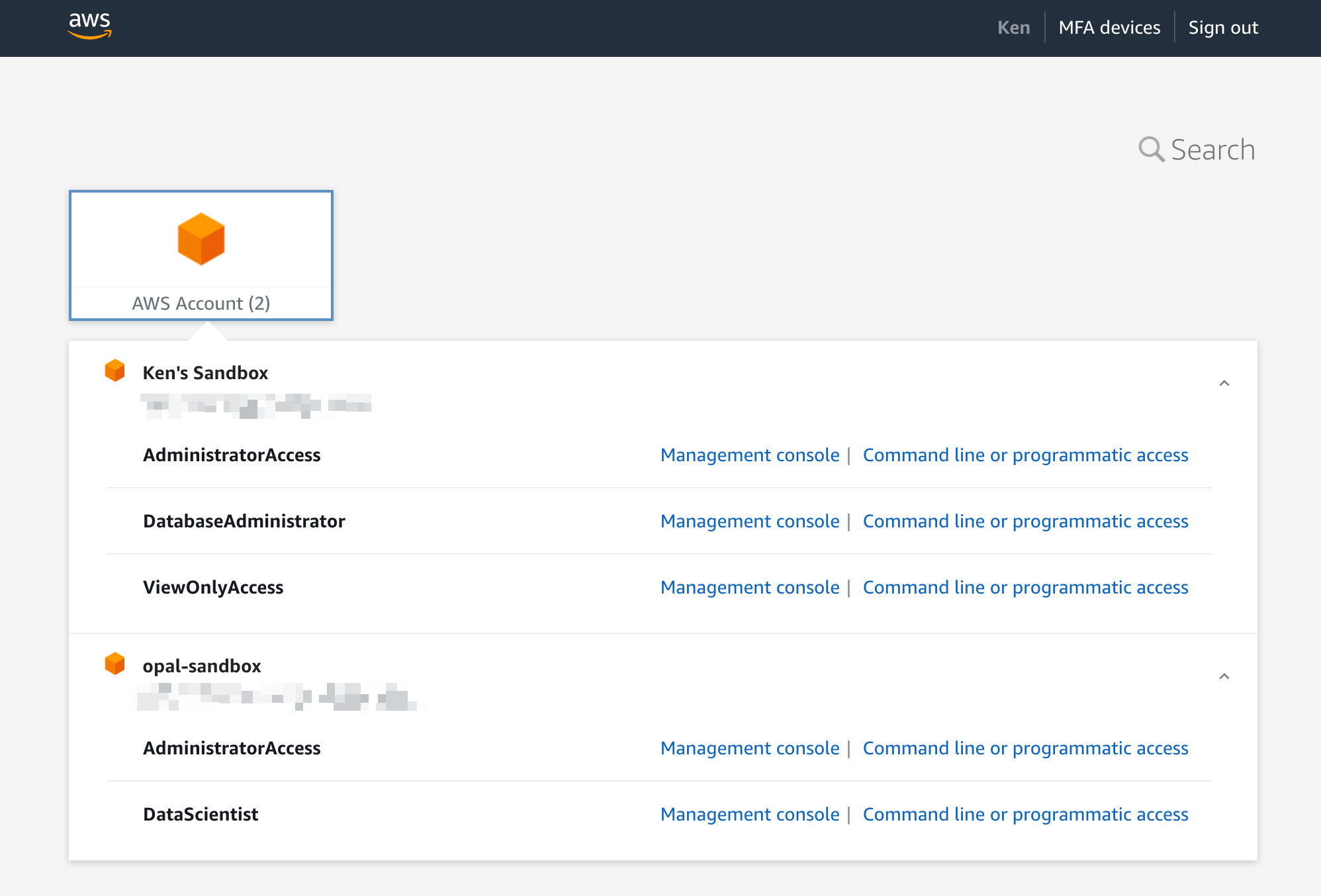
As with any other resource, IAM Identity Center Roles can be requested by users either through Opal’s web UI or through Slack. AWS Account resources serve as containers and cannot be requested or assigned directly to users or groups. Once a user gains access to a role, they can click the Connect button to directly link to the AWS Access Portal from which they can gain console access or CLI access credentials for the desired role.