This guide assumes you’ve already configured your AWS organization in
Opal.
Supported RDS engines
Amazon IAM database authentication is available for the following database engines:- MySQL 8.0, minor version 8.0.16 or higher
- MySQL 5.7, minor version 5.7.16 or higher
- MySQL 5.6, minor version 5.6.34 or higher
- PostgreSQL 14, 13, 12, and 11, all minor versions
- PostgreSQL 10, minor version 10.6 or higher
- PostgreSQL 9.6, minor version 9.6.11 or higher
- PostgreSQL 9.5, minor version 9.5.15 or higher Don’t see what you want here? Let us know by suggesting an edit or reaching out and we’ll make it happen.
Add an RDS database
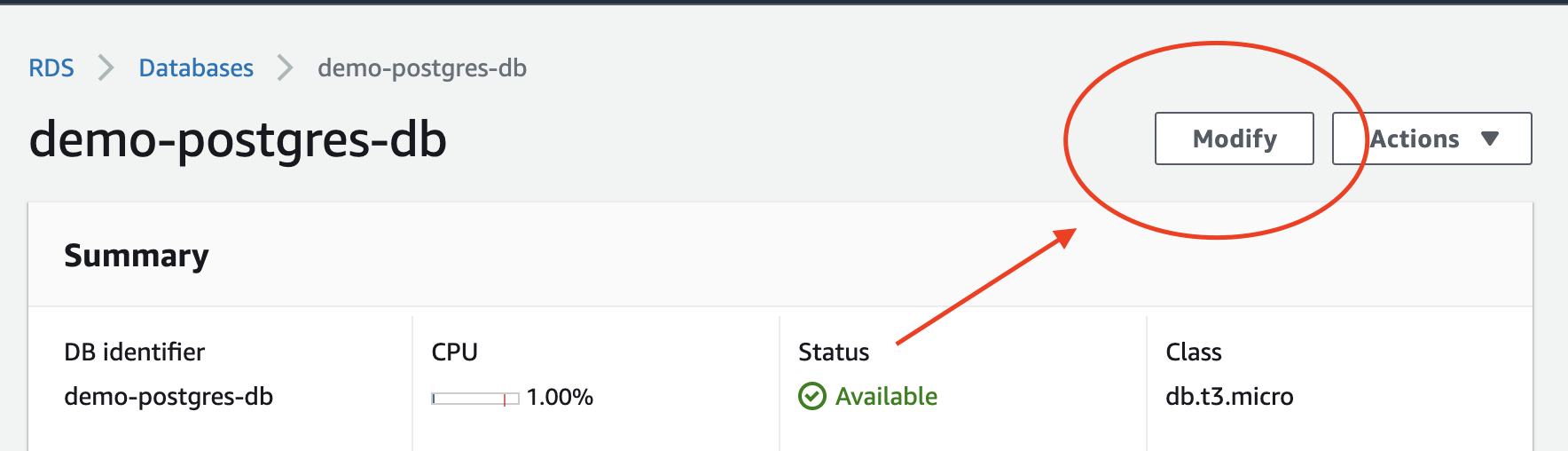
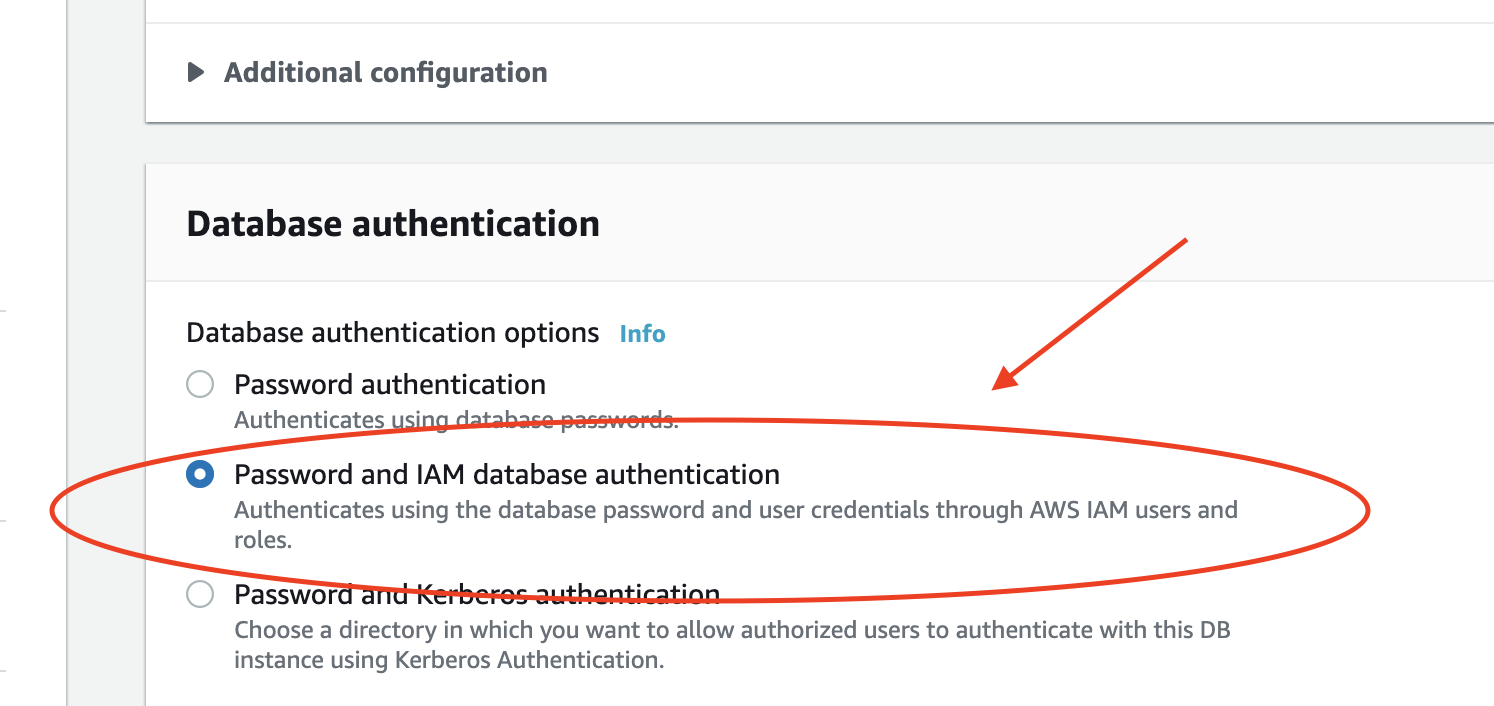
1. Enable IAM authentication
You’ll need to enable IAM database authentication for your RDS instance. You can do this using the AWS Console and CLI. You can read more on how to do this here in the AWS official documentation.AWS Console
AWS CLI
2. Create database users
Connect to your database and create a database user with read-only access. Here is a snippet you can use for Postgres and MySQL.Custom Database Users
If you’d like to instead define your own database users with custom amounts of access, you can do that easily in one of two ways: through Opal UI, or with tags.Opal UI
- In the Inventory, go to the Roles tab of the RDS instance, then select + Create.
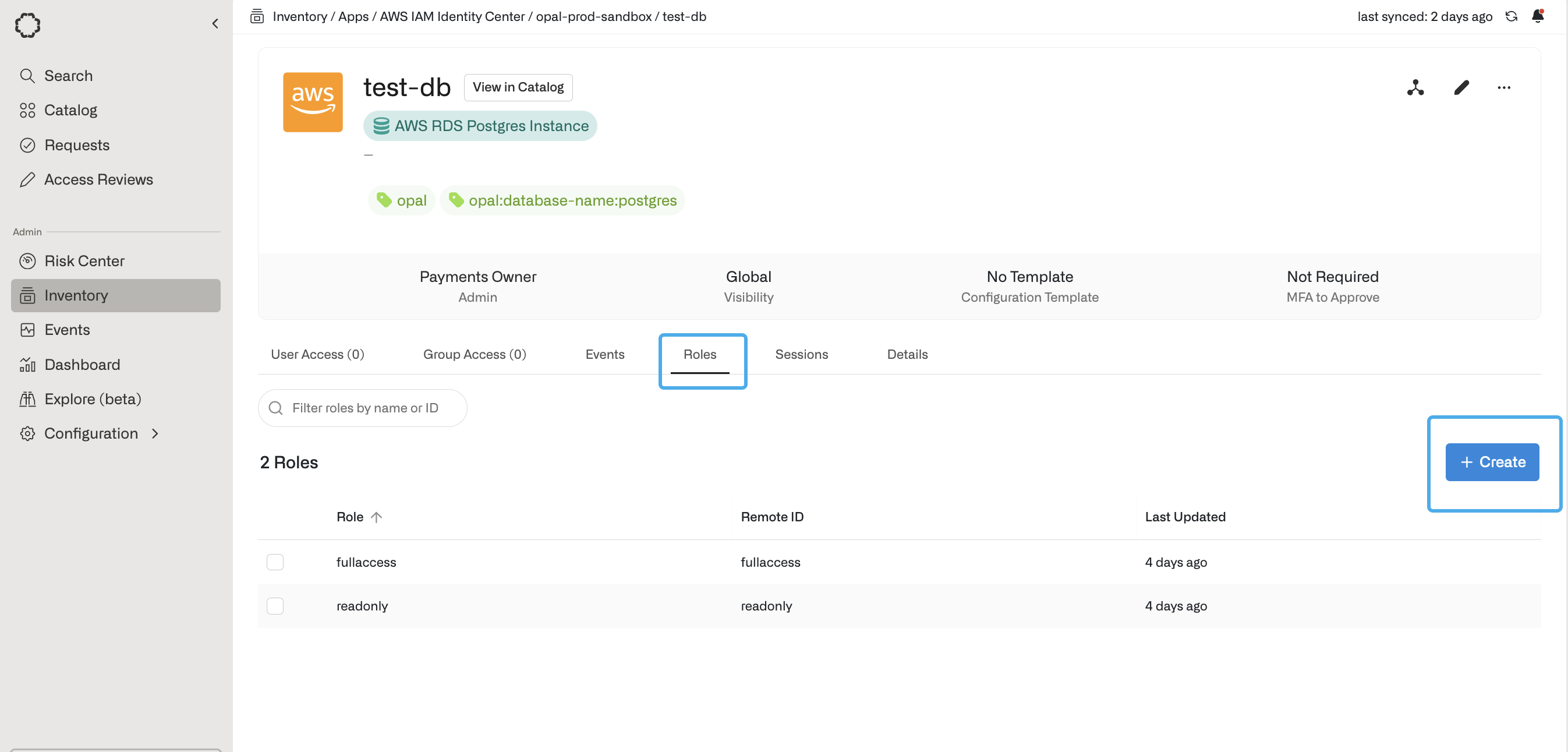
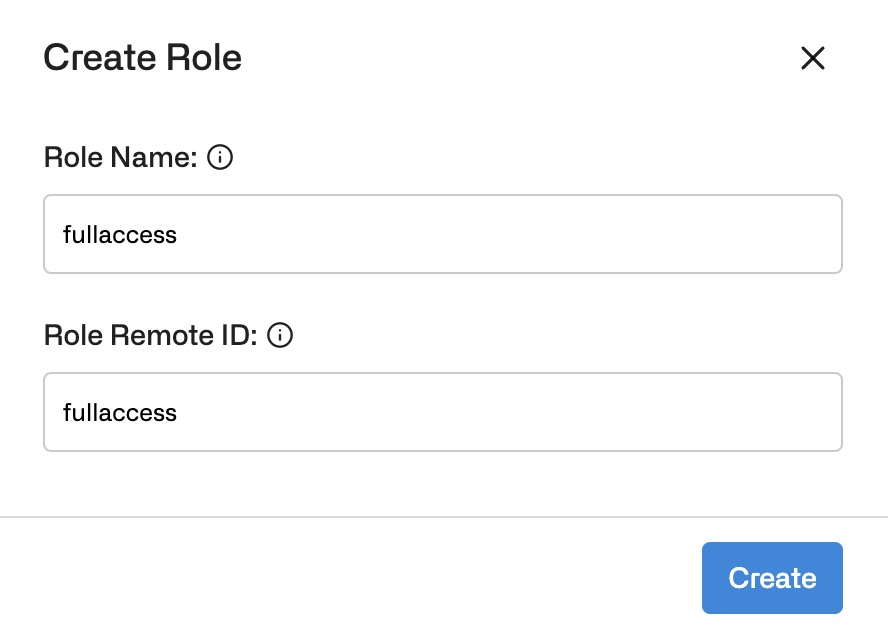
- Add a role name, and the database username as the Role Remote ID, then select Create.
Tags
- Create the user with any username that you like and grant them
rds_iamwith the following queries:
- Tag the RDS database with key
opal:user:1and valuemyuser. You can manage multiple levels of access using more tags! Example:opal:user:2=>myseconduser. To see how to tag your database check out Step 3.
3. Tag the database
Finally, tag the RDS database withopal so Opal knows which RDS databases you’d like Opal to automatically import:
AWS Console
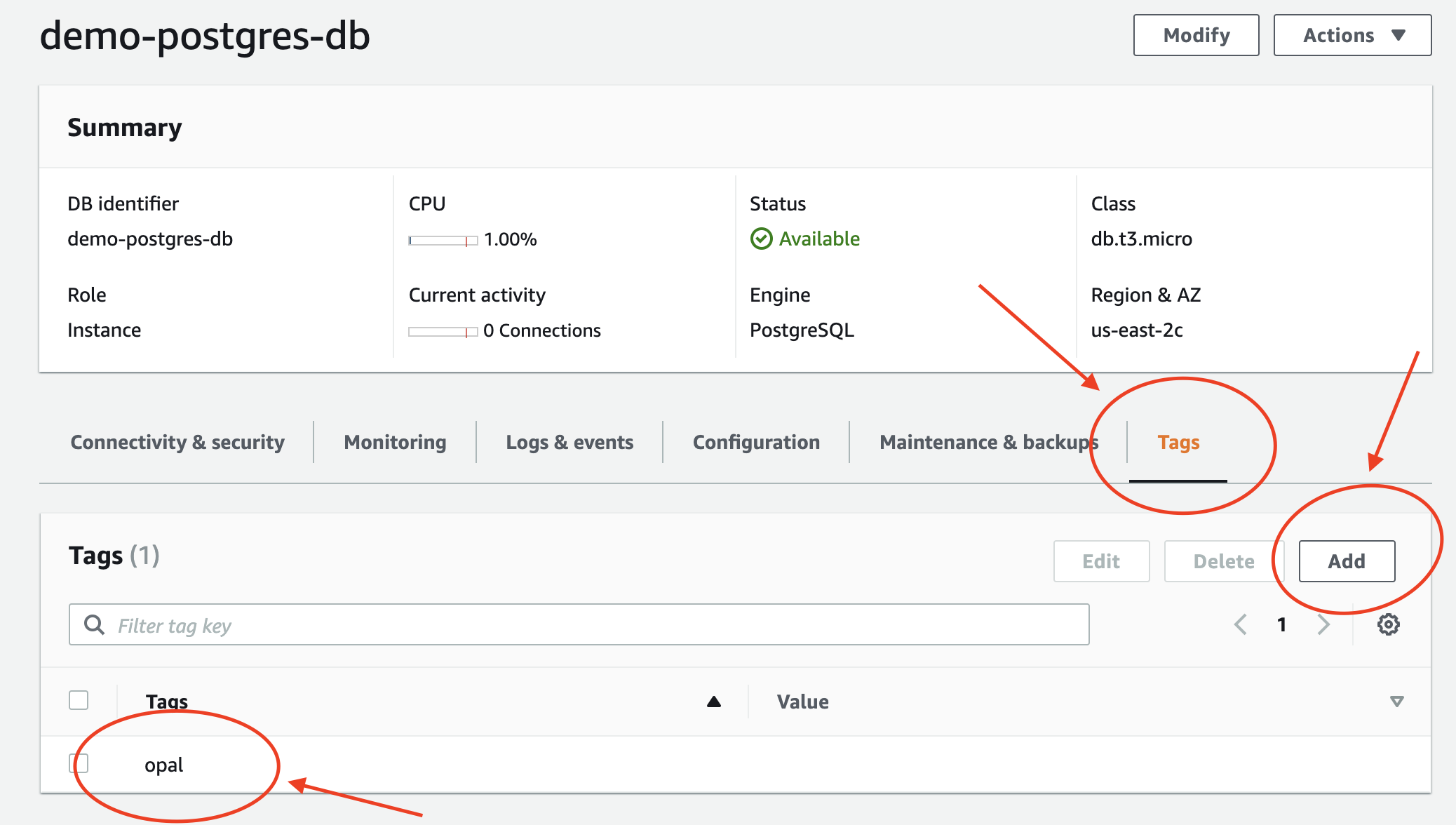
opalAWS CLI
Terraform
Add the followingtags argument to your AWS RDS instance:
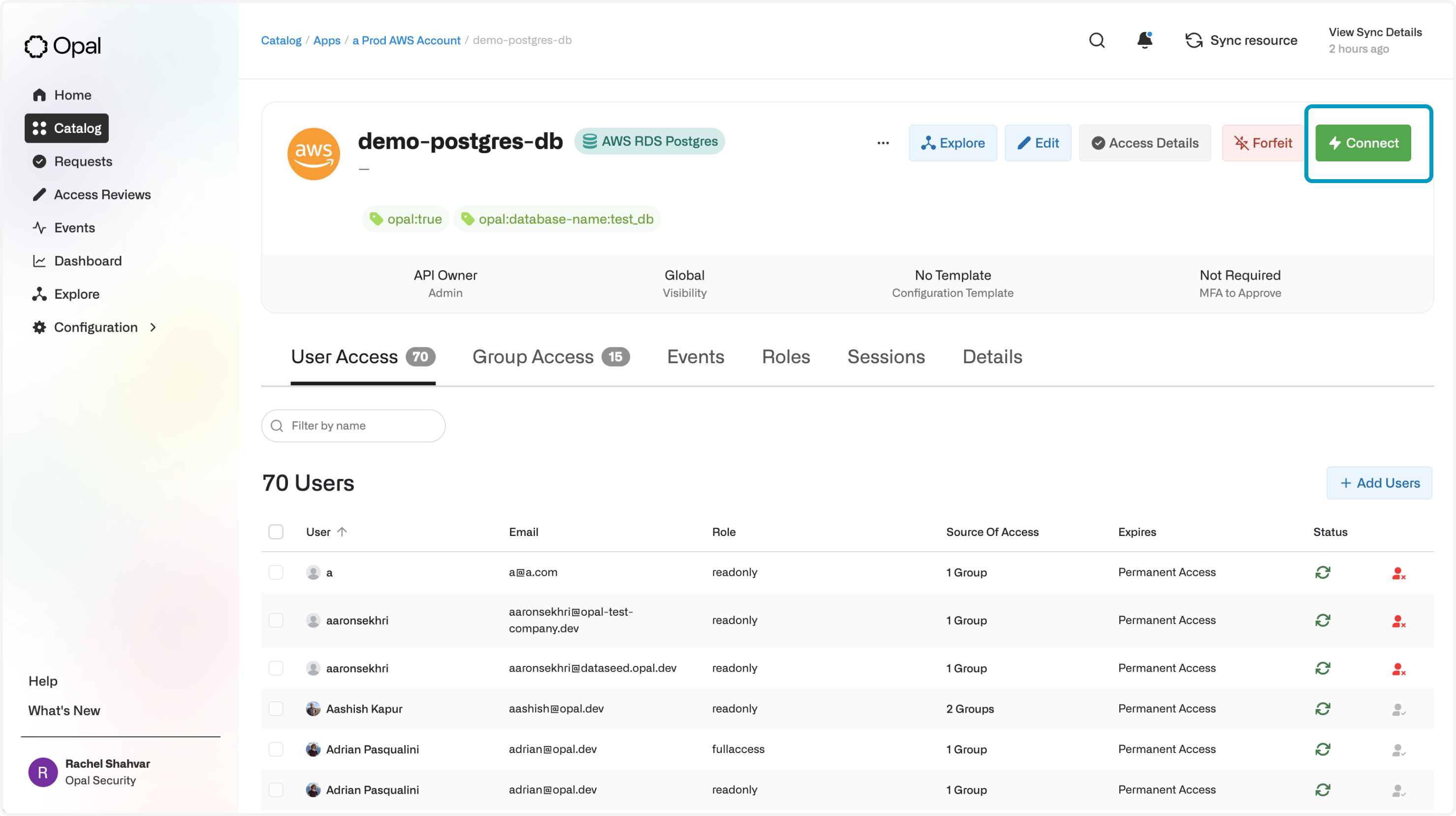
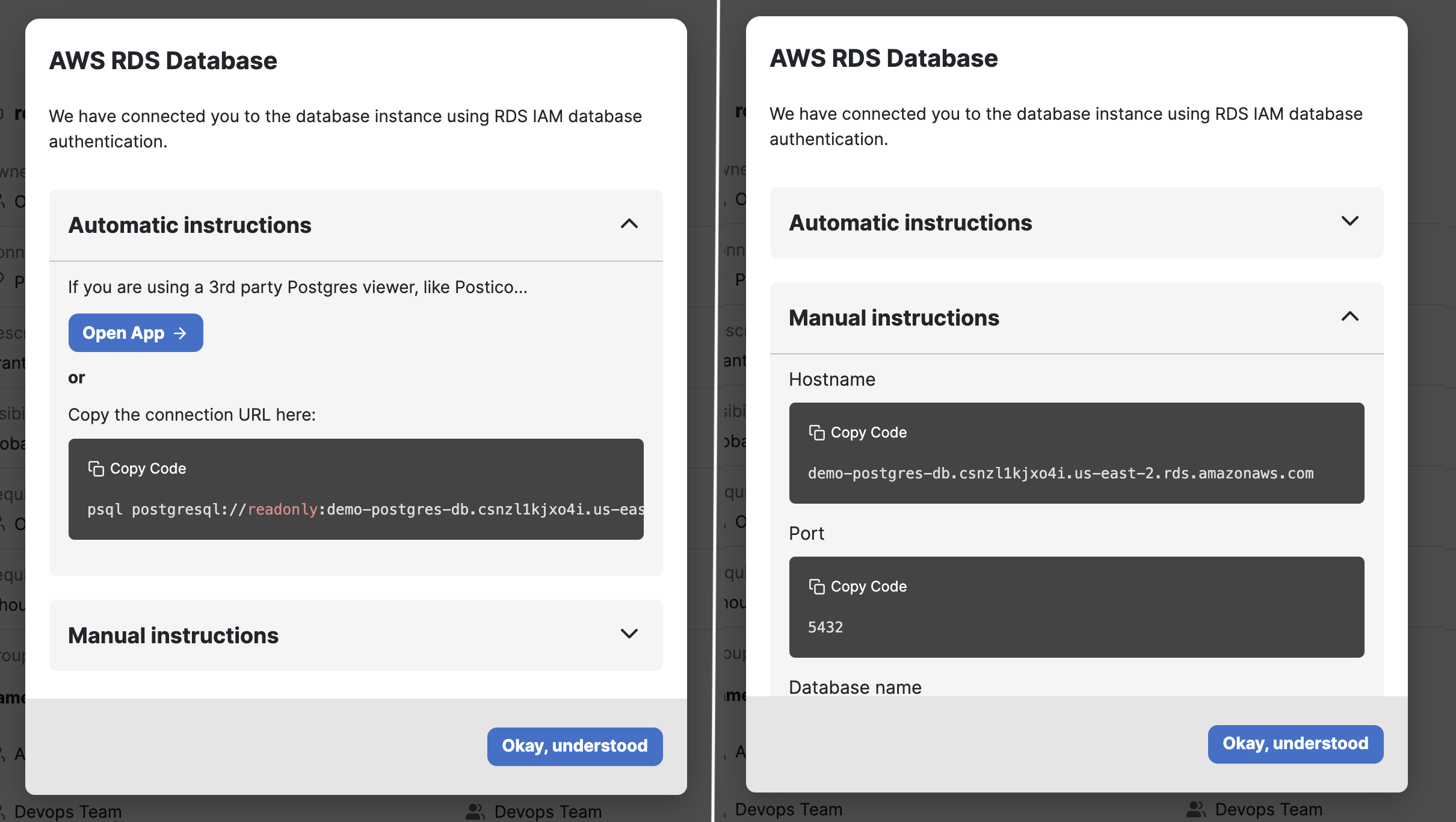
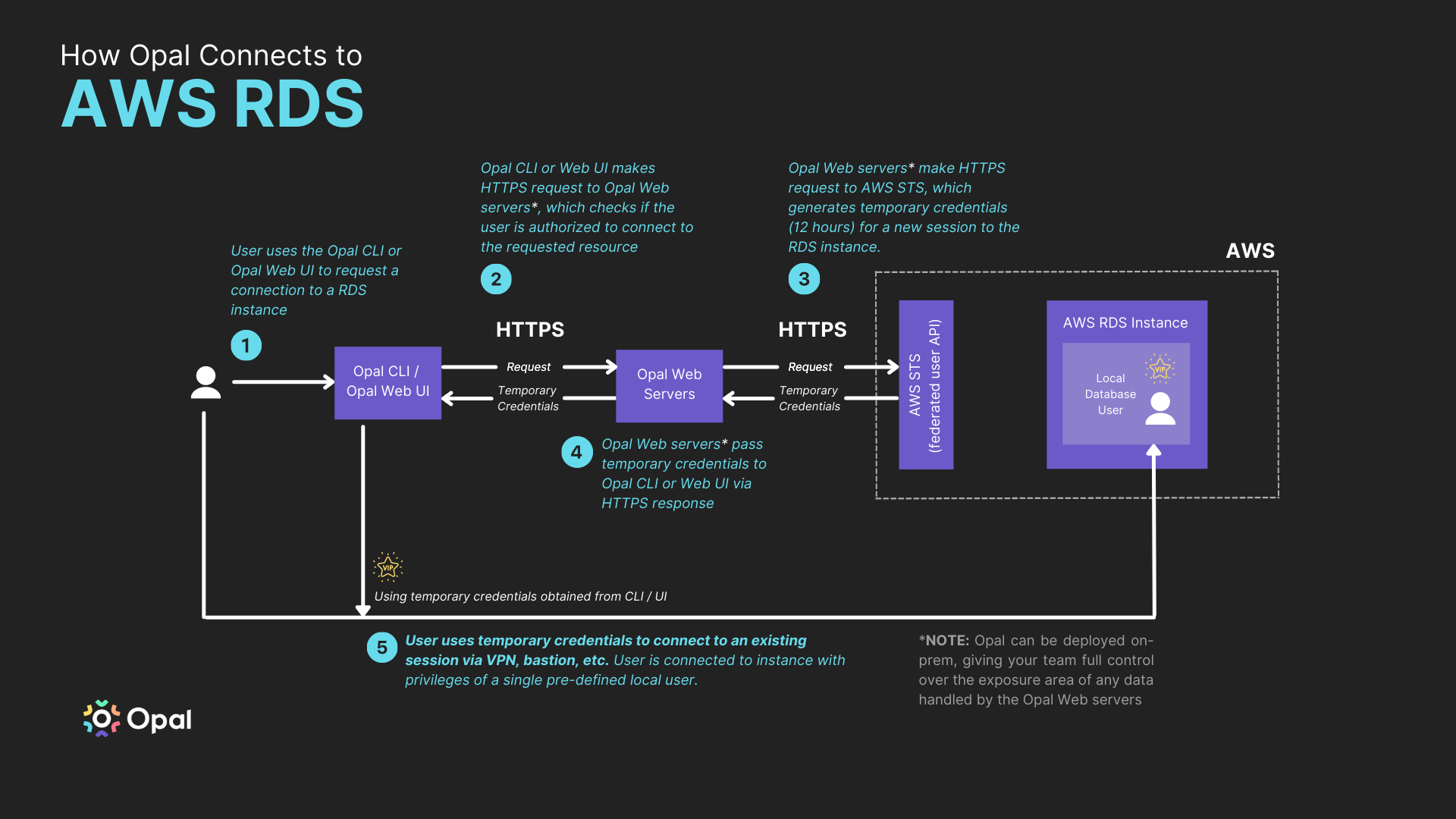
Access an RDS database in Opal
Once you’ve successfully tagged an RDS database, it will appear on the Resources page in the Catalog. If you followed the steps above, you’ll be able to Connect with read-only and full access to your database. Access to RDS databases in Opal is session-based, meaning your developers won’t have access unless they initiate a session.