This guide assumes you’ve already configured your AWS organization in
Opal.
Add a role
Use the following steps to connect an IAM role to Opal.Trust policy
You must use the following trust policy for your role, substituting as follows:${ACCOUNT_ID}: The account ID of the account being configured.${IDP_ISSUER_URL}: The Identity Provider’s issuer URL${OPAL_CLIENT_ID}: The Client ID assigned to Opal via your IdP.
Create a role
Here is an example invocation for creating a role with the above trust policy file:Attach policies to a role
Next, attach all the policies you want to show up in Opal under this role. You can do this in the AWS Console: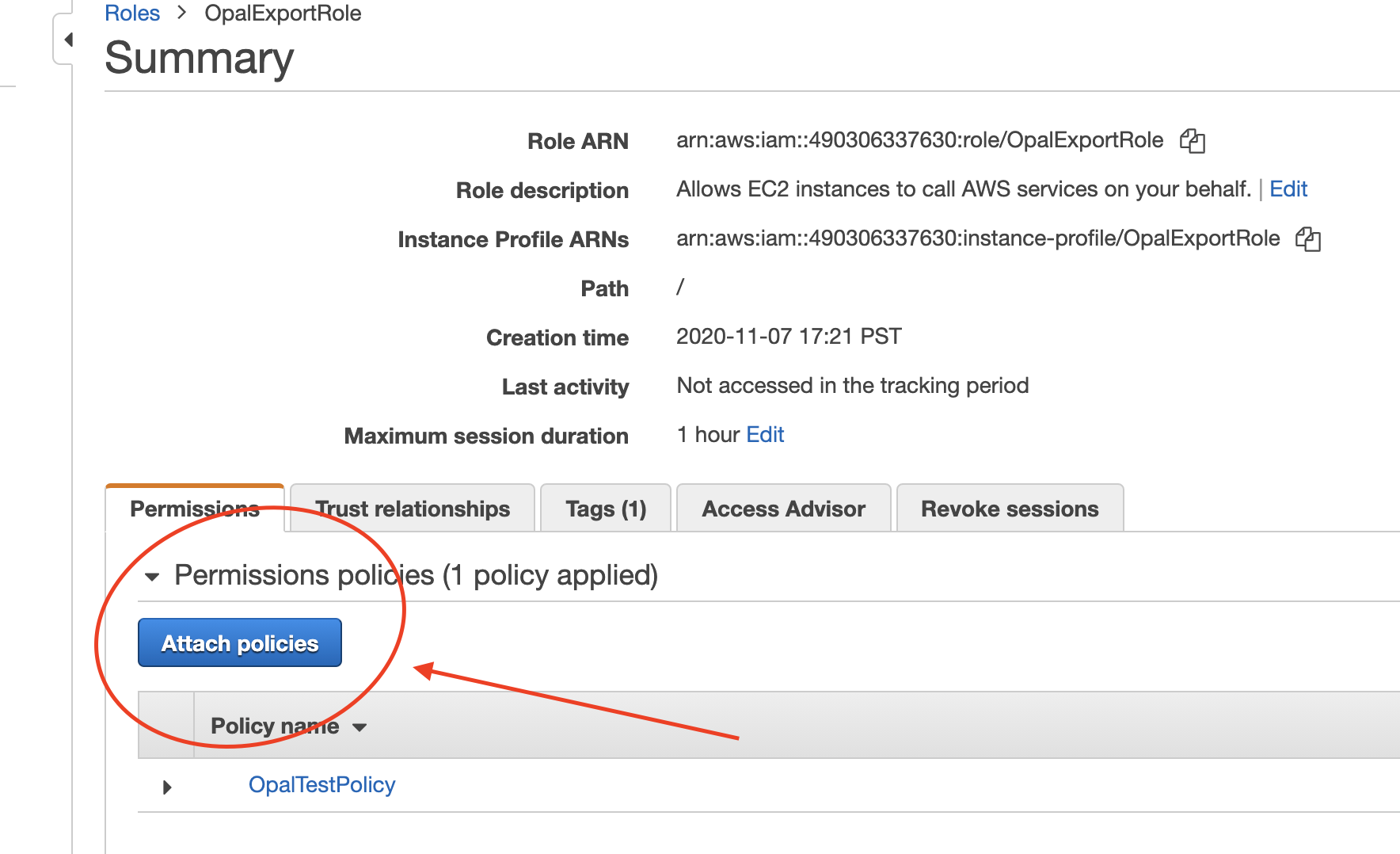
Terraform
If you use Terraform, for an existingaws_iam_role, you can use the following arguments for the role you want to manage with Opal:
aws_iam_role via the aws_iam_role_policy_attachment resource.
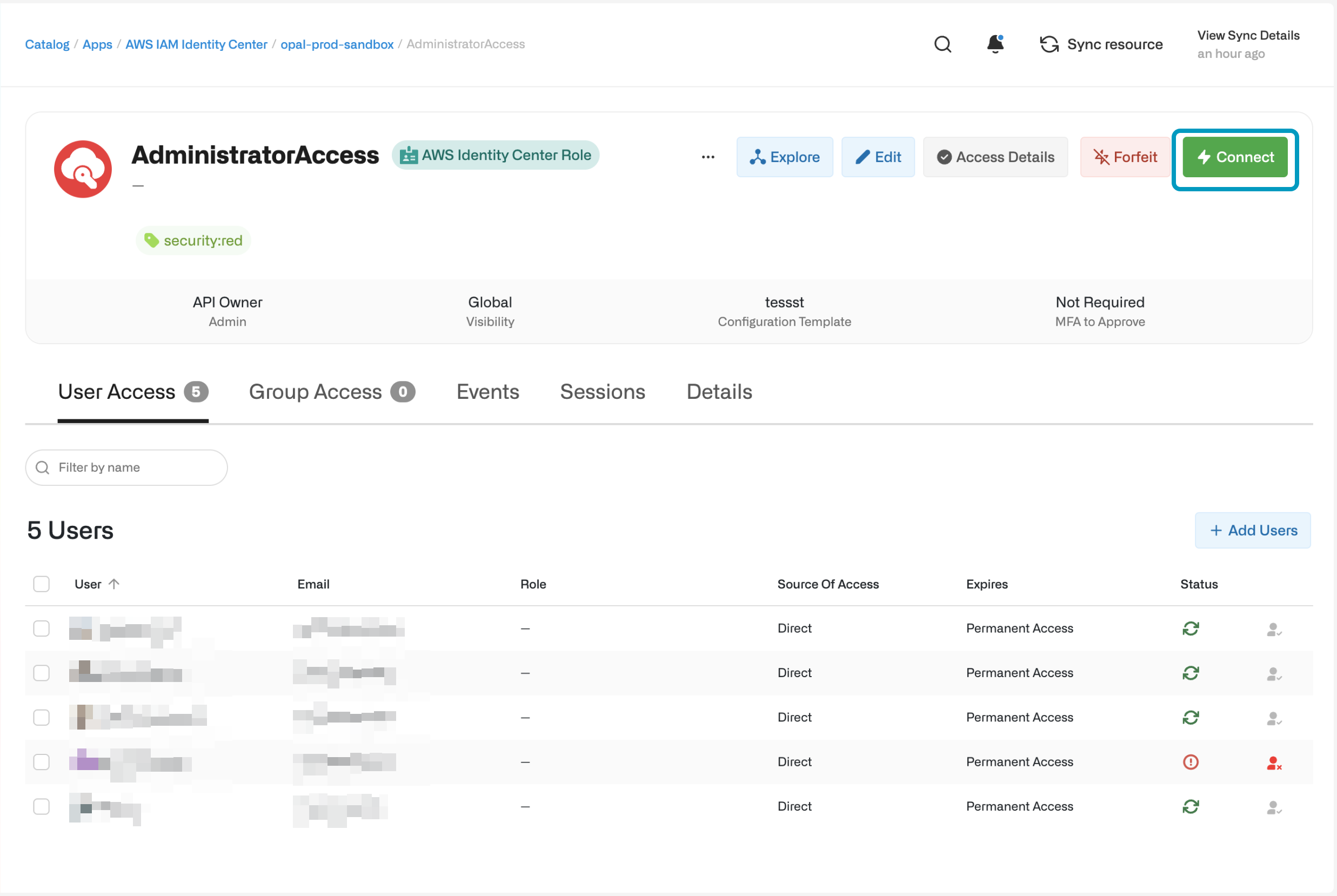
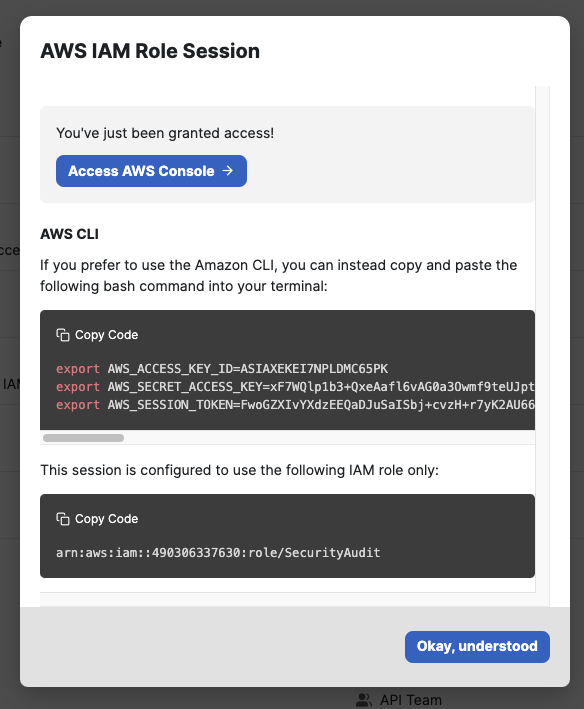
Access roles in Opal
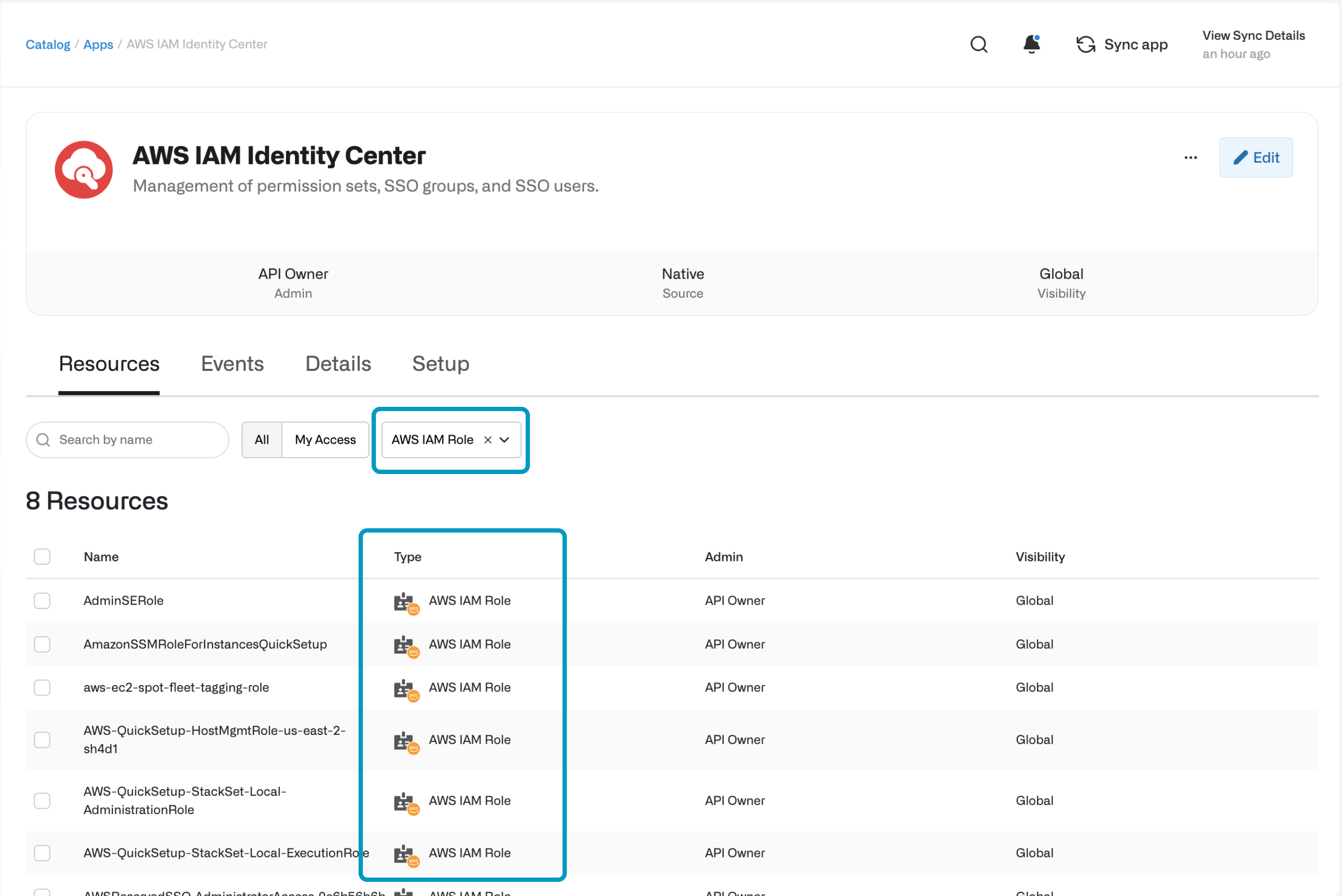
Import roles by selecting the … > Import items from the Inventory. After you’ve imported roles to Opal, users can request them from the Catalog and you can manage them from the Inventory.