- Azure SQL Databases
- Azure SQL Managed Databases
Prerequisites
Enable Microsoft Entra ID authentication for your database.1. Enable Microsoft Entra ID Authentication on SQL
For SQL Databases, go to its parent SQL Server and enable Microsoft Entra ID Authentication. For SQL Managed Databases, go to its parent SQL Managed Instance and enable Microsoft Entra ID Authentication.2. Add Opal IP addresses to your firewall rules
On the left hand side, under Security > Networking, add the following IP addresses to your SQL’s firewall rules. If you self-host Opal, these will be different.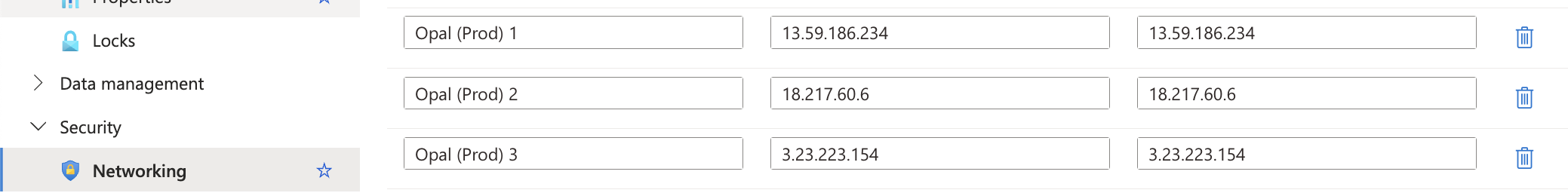
3. Add your company addresses to your firewall rules
If your company uses a VPN, add any IP ranges to the firewall rules. If you don’t add them, each user will have to add their unique IP address and you can easily hit Azure’s 128-firewall rule limit.4. Assign the managed-identity permissions
- Go to the SQL Server or SQL Managed Instance,
Security->Identity. UnderSystem Managed Identity, toggle the status toOnand save this setting. - Go to
Microsoft Entra ID, on the left hand panel,Manage->Roles & Administrators, find theDirectory Readersrole and click on it. - Click
Add Assignmentand add the SQL Server or SQL Managed Instance Managed Identity.
5. Add Opal as an Admin
If you have an existing admin:- Create a new Azure Security Group:
SQL Admins - Add your existing admin to the
SQL AdminsSecurity Group - Add Opal’s service principal to the
SQL Adminssecurity group
db_datareader and db_datawriter roles.
